
Anom Encrypted App Prognosis
ANOM EXPOSED VS CIPHR
I did a comparison between both CIPHR and ANOM after receiving a message mentioning ANOM became as soon as this and this while CIPHR became as soon as in a problem to be infiltrated (which isn’t any longer TRUE) so I sure to create some of my have confidence testing.
To deliberate let’s inaugurate with some answers to one of the most most statements made by ANOM:

– Yes Ciphr does use UEM but they are wrong about an EXPLOIT being made by Blackberry as every replace through UEM that’s remotely pushed to the cell machine would should always be in my thought signed by the encrypted keys that Ciphr setup for their very have confidence infrastructure. Most efficient Ciphr has access to these keys
– A Tool is signed in my thought with it’s have confidence operate of keys derived from Ciphr and delivered through Blackberry UEM working in unison with the Samsung Knox Security Machine. Not even Blackberry can push updates without this signed key by Ciphr for functions working on Ciphr phones. Ciphr phones are additionally locked down with custom insurance policies to prevent them from doing one thing without prior authorisation by Ciphr. Here is an ENTERPRISE MILITARY GRADE Encrypted setup.
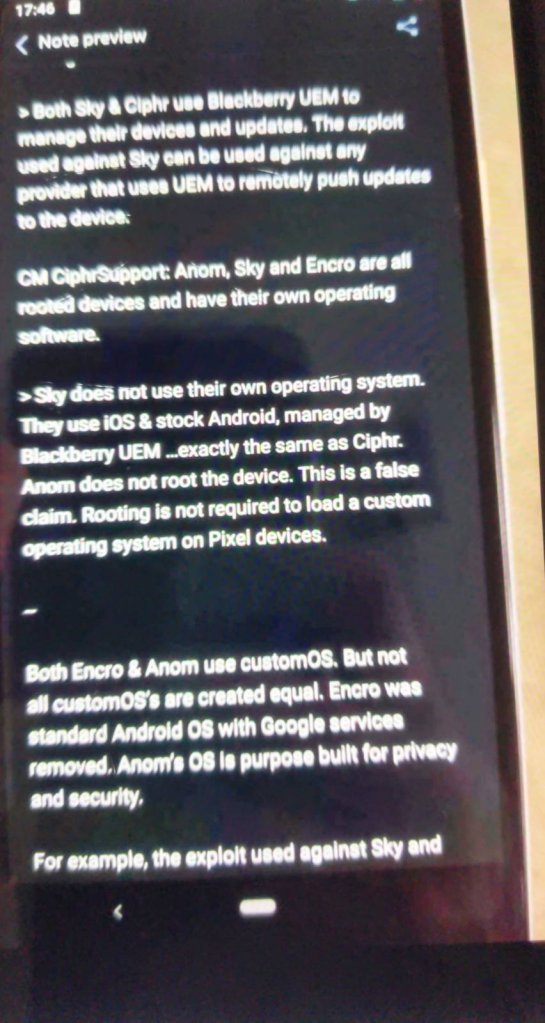
– Appropriate Ciphr does use the Inventory Android Working machine with special Endeavor level Encryption and customisations on their network as properly as their handsets which additionally contain hardening making it one of many most stable handsets in the World. Personalized community insurance policies done by Ciphr additionally prevent access to anything else different than the BLACKBERRY UEM Server which is a tunnel which then connects to the Ciphr Offshore Proxy Server through a stable and Encrypted Armed forces Grade Encryption. Updates can only be authorized by Ciphr making it one of many most stable and locked hardened locked down handsets in the World. All functions must have authorisation from both Ciphr & their Endeavor grade policy level settings modified with the Ciphr Access Keys to access anything else beyond the Blackberry UEM Firewall & the Ciphr Encrypted Offshore Servers. Despite the indisputable truth that Blackberry UEM became as soon as a technique or the opposite compromised, due to Blackberry’s incapacity to signal with the Ciphr Encrypted Key then it would possibly perhaps perhaps tranquil no longer be that it is most likely you’ll perhaps perhaps most likely also judge of to force compromised updates to any Ciphr units by any capacity.
-ANOM this assertion about Rooting is wrong, Rooting is required to set up a custom android working machine on any pixel machine or android machine any machine except it has been signed specifically by the handset producer. Anom has initially rooted their machine by merely unlocking the android boot loader which secures file integrity and then installed their very have confidence custom android working machine followed by locking the boot-loader yet again with their very have confidence keys, unheard of love now we have our have confidence signed keys for utilizing Blackberry UEM, ANOM has their very have confidence keys for the Working Machine. In line with my testing ANOM’s custom android OS unfortunately has many extra evident flaws inside it’s create and updates loads much less than the extraordinary inventory Android OS making it physically susceptible if it were to fetch into the infamous hands no longer to mention it has no custom community insurance policies or constructed in firewall to live the android os working machine from gaining access to google remotely. For sure upon a visual DISPLAY of all telecommunication connections I became as soon as moderately concerned to glance the amount of IP addresses touching on to many corporations all over the 5 eyes Governments (Australia, USA, Canada, UK, NZ who share data with one one more) and to create issues worse they were disclose connections to the bellow proxy servers and loads of others giving me the capacity to to find their far away offshore Romanian Server with an IP of 193.27.15.41:
ip: “193.27.15.41”
metropolis: “Bucharest”
operate: “Bucure?ti”
country: “RO”
loc: “44.4180,26.1691”
org: “AS9009 M247 Ltd”
postal: “020331”
timezone: “Europe/Bucharest”

– ANOM is infamous to inform that their Android Working Systems reason is constructed for Privateness and Security. Some google companies are no longer removed or blocked by even a VPN or Firewall.
-This setup aged by ANOM presents Google the capacity to fingerprint their machine and computer screen it remotely in a DIRECT formulation without a safeguards in inform in any admire throughout the accumulate. The ANOM machine I examined professionally became as soon as in actuality in fixed contact with Google servers which became as soon as moderately referring to. The following IP’s 216.58.200.99 & 142.250.70.196 both lead abet to Google servers in both NSW, Australia and California, USA.
– ANOM has a setup extra at possibility of assault as they don’t even use a stable VPN or FIREWALL to even safeguard utilizing their APPLICATION remotely, which manner consider you were assembly up with anyone love an EX-LOVER your partner can also merely no longer approve of (unheard of love a VPN protects you from inaugurate air entities seeing which web sites or messaging methods you make use of) you’ll be succesful to create this boring closed doorways all over the confides of a HOTEL room.
– With ANOM’s setup consider assembly up with that particular EX-LOVER your partner didn’t approve in beefy public witness without a safeguards in inform. Eavesdroppers who will most definitely be in quest of to search out ANOM users over the cell telecommunications network. ANOM without plight presents this data away when their phones are consistently BROADCASTING without the ANOM utility even being opened on their units to the following IP addresses 99.83.192.129, which leads to anom.io and then while utilizing their provider the following IP’s are leaked consistently as packets while utilizing the utility:
75.2.32.148 – amazon web server USA – Proxy
35.171.36.131 – Amazon Internet Servers – Proxy
76.223.70.181 – Amazon Internet Servers – Proxy
35.176.253.60 – Amazon Internet Servers – Proxy
75.2.90.136 – Amazon Internet Server USA – Proxy
169.46.82.180 – logs5.papertrailapp.com – Faraway Logging App
216.58.200.99 – Google Servers
142.250.70.196 – Google Servers
99.83.192.129 – anom.io – Here is shown without even opening up the utility inside Calculator
13.248.215.128 – Voiceping router (Outdated maybe for their Walkie Talkie Talk Characteristic) – voicepingapp.com
– If for some particular reason an replace server became as soon as a technique or the opposite breached and malicious code became as soon as uploaded, it tranquil would no longer create it to a CIPHR machine as the replace/utility needs to be signed with the CIPHR keys earlier than it’ll even be sent by Blackberry UEM Encrypted Server.
– Sky ECC can only be infiltrated from the INSIDE by a rogue employee who gave authorities access to the Sky Signed Certification Keys which gave authorities the capacity to access the Sky Machine and to find their servers and push rogue updates without the Sky Builders spellbinding except the because it became as soon as officially signed with their certificates without their data due to a rogue employee working on the inside.
– In line with ANOM their assertion “If our replace server became as soon as hijacked as became as soon as the case with ENRO and SKY the attacker would no longer be in a problem to set up malicious code on the machine. The an identical can no longer be said for suppliers that use particular person grade working methods managed by Blackberry UEM” is vastly wrong.
— CIPHR runs both the Blackberry UEM VPN and their very have confidence True Encrypted Offshore Servers alongside Customised Endeavor Grade Work Policies which limits the units performance for both Endeavor Safety and Security. For sure unheard of love what took place with unfortunately ENROCHAT when their servers were infiltrated bypassing the Blackberry UEM altogether the an identical can without plight be said for ANOM who don’t even use a VPN to safeguard anyone in actuality utilizing ANOM. For oldsters that knew a particular person aged ANOM you’ll be succesful to without plight be in a problem to name all users over the fashioned telecommunications network without decrypting any of their communications in any admire, one thing it is most likely you’ll perhaps perhaps most likely no longer merely create with CIPHR let alone know that particular individual is infrequently utilizing a CIPHR phone, appropriate anonymity,
-ANOM have incorporated many aspects from already on hand apps comparable to the VOICEPING APP that manner you additionally must depend upon VOICE PING APP for securing your encrypted communications which works with their Walkie Talkie Performance, there are hundreds of similarities between that utility and ANOM, one thing which appears to be like to fright anyone if PRIVACY and ANONYMITY are your #1 diagram. With ANOM I became as soon as in a problem to to find all of their PROXY servers including their MAIN servers with minimal ease, all working all over the 5 eyes alliance. About the one thing ANOM is dazzling at is spreading misinformation without presenting the information.
ANOM uses the following for their utility:
– JIRA for tracking duties as properly as Q & A
– Wire Messenger (Free utility love wickr) for Conversation (Their head inform of enterprise is in america)
– Agile Pattern
– Jenkins for their builds after they push updates (Your relying on ANOM to stable your communications after they’ll’t even stable their very have confidence servers from eavesdropping).
– SQL Lite Database for storing USERS Knowledge
– Now if ANOM is so all in favour of safety and safety I would fix their entire setup which looks upright as rotten as a conventional android handset working WICKR. If the authorities were to access ANOM’s server of 193.27.15.41 in ROMANIA which is a third world country that can perhaps perhaps most likely also merely inform they buy privateness significantly but as the feeble asserting goes “shit walks, money talks” they would perhaps perhaps without plight infiltrate their Offshore Romanian Server and set up special hardware units on those servers without ANOM’s data.
Authorities would possibly perhaps perhaps entirely infiltrate every users units as properly as their operations and worse of all authorities would be succesful to decrypt and intercept their messages unheard of love what took place with ENROCHAT. . ANOM states they have confidence the infrastructure but this couldn’t be additional from the truth, they hire their servers off different entities that manner they don’t have beefy preserve watch over over their servers. But another formulation they would perhaps perhaps infiltrate ANOM is by having access to FIELDX.io who maybe constructed their customised Android OS as the company is owned by a particular person in FRANCE, acquiring a warrant would no longer be complicated.
– To create off my testing I did truly ticket the an identical assessments on CIPHR and the one server I became as soon as in a problem to glance became as soon as the Blackberry UEM Encrypted VPN, nothing extra or much less. Here is completely moral and to any inaugurate air entities monitoring they would no longer even be in a problem to snarl whether or no longer your verbal change machine became as soon as for CIPHR or different Endeavor linked functions.
– ANOM additionally states their company is in PANAMA, that will most definitely be the case but their servers are no longer located in PANAMA let alone owned by them which manner any cheap authority will most definitely be in a problem to access their servers with relative ease.
Extra data referring to ANOM:
anom.one 75.2.32.148
anom.one 99.83.192.129
conference.anom.one 75.2.32.148
conference.anom.one 99.83.192.129
share.anom.one 75.2.32.148
share.anom.one 99.83.192.129
logging.anom.one 18.134.176.181
talk about.anom.one 75.2.25.172
xmpp.anom.one 75.2.32.148
xmpp.anom.one 99.83.192.129
genesis.anom.one 18.134.176.181
vpprxy.anom.one 76.223.70.181
vpprxy.anom.one 13.248.215.128
www.fieldx.io (aged to preserve watch over the ANOM DEVICES)
STAY AWAY FROM ANOM IF YOU VALUE YOUR PRIVACY & SAFEY, THEY ARE COMPROMISED, LIARS AND YOUR DATA IS RUNNING VIA USA – Passed onto LAW ENFORCEMENT and different Entities