
More and more malware is the utilization of Discord’s CDN for abuse
A sizzling potato: When talking about “abuse” when it comes to smartly-liked instantaneous messaging carrier Discord, it would possibly well in total be about the community chat platform being worn by trolls or for hateful and NSFW state material. But Discord’s state material transport network (CDN) is now more and more being worn to host malicious recordsdata and hand out malware through hyperlinks that seem official.
A file by Sophos has uncovered the scale and range of malware the utilization of the Discord’s CDN: “Sophos merchandise detected and blocked, magnificent within the previous two months, almost 140 cases the option of detections over the identical interval in 2020,” talked about authors Sean Gallagher and Andrew Brandt, with 17,000 engrossing URLs learned pointing to malware within the 2d quarter of 2021.
And these 17,000 URLs are most effective counting malware hosted by the carrier, which keeps recordsdata on Google Cloud and uses Cloudflare as a frontend. The massive figure excludes malware hosted in diversified areas that makes use of the infrastructure equipped by the CDN; Discord’s chatbot APIs had been worn for report-and-tackle watch over of malware in infected targets, as smartly as for exfiltrating stolen info into inside of most servers.
Malware the utilization of the platform varies, nonetheless in step with the authors the bulk of it is centered round info theft, both through notify credential-stealing or faraway earn entry to trojans (RATs). Threats targeting Android platforms had been additionally viewed, ranging from advert-clickers to banking Trojans, as smartly as expired ransomware that lacked any methodology to pay the attackers.
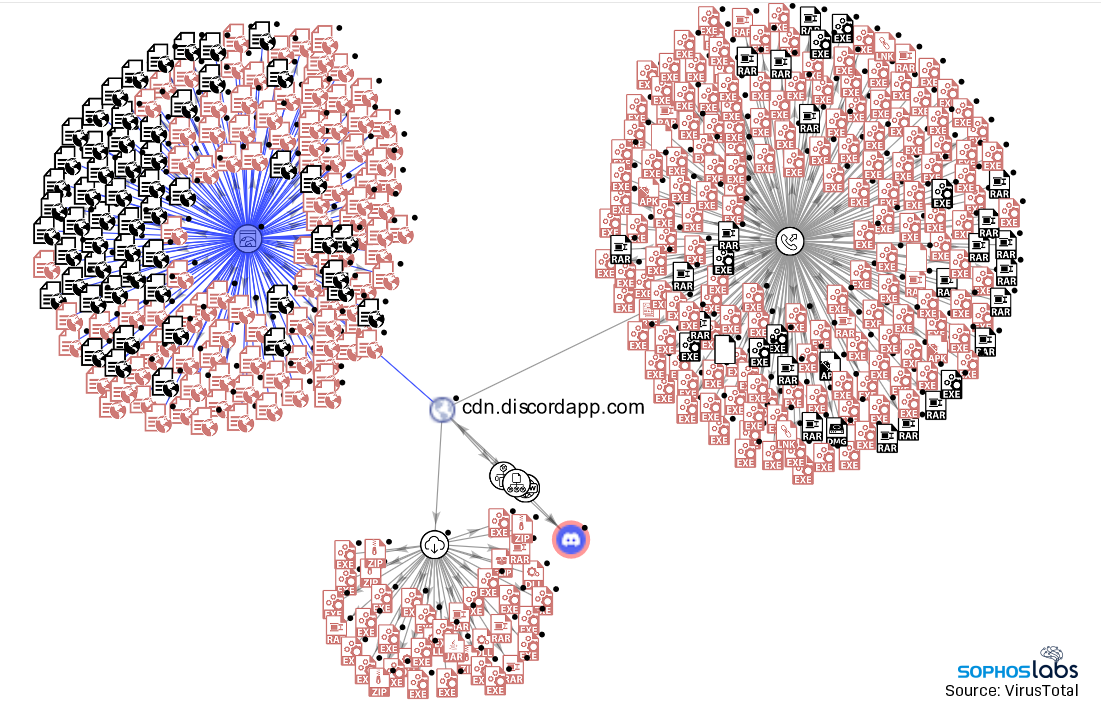
Visualization of a runt section of malicious (red) and benign (sunless) recordsdata hosted on Discord’s CDN.
Discord is a most stylish messaging platform that used to be firstly centered at gaming communities, and they continue to hold a noteworthy presence on the platform, so it be not magnificent that barely so much of the malicious recordsdata hosted and distributed on it are tied to gaming.
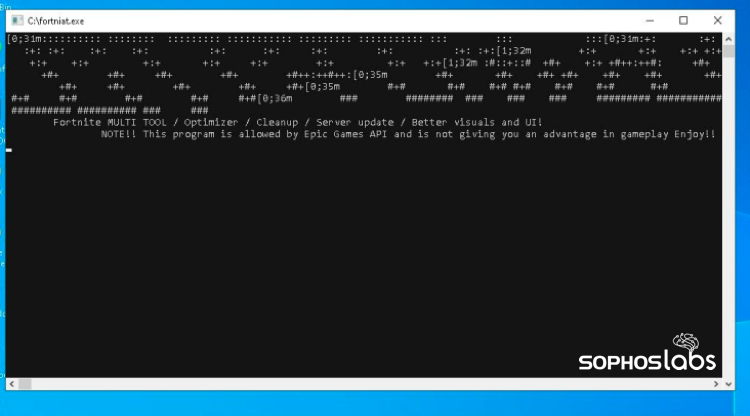
To illustrate, researchers identified a modified Minecraft installer that additionally captured keystrokes, screenshots, and camera pictures, as smartly as a “multitool for FortNite” (sic) that infected programs with a Meterpreter backdoor.
Others centered Discord itself, stealing credentials and authentication tokens, or disguised themselves as instrument ranging from inside of most browsers to cracked Adobe functions.
Social engineering used to be additionally in total a ingredient, with the promise of generating keys for Discord’s premium Nitro carrier usually worn to bait customers. One instance directly attempted to search out and assassinate off processes for dozens of security instruments, as smartly as built-in Windows protection choices — even supposing if it be any consolation, like the aforementioned ransomware, barely so much of these trojans had been extinct sufficient that they had been attempting to phone home to servers that weren’t round to reply.
Within the kill, the freemium model that Discord depends on for its accessibility works in opposition to it here. Whereas many quality-of-lifestyles choices neat to benign customers are paywalled within the back of Nitro, free accounts are serene fully in a jam to upload recordsdata (albeit with a size limit) and pronounce with its APIs.
This permits threats to pop up time and time all any other time with novel accounts; while Discord took down phenomenal of what used to be identified by the researchers, they came upon that novel malware used to be continuously being uploaded or communicating with Discord.