Make investments in cyber security with confidence using a structured come
Cyber security has by no approach been more tense or crucial in impulsively altering enterprise, regulatory, IT and threat environments. There might be a want for a more structured come to investment
The cyber security bother has by no approach been bigger thanks to the repeatedly increasing attack surface as the shift to mobile, cloud and various applied sciences supporting digital transformation beneficial properties momentum. These applied sciences provide increasing opportunities for attackers. On the an identical time, attackers are changing into ever better skilled, organised and resourced to manufacture ever-increasing volumes of malware and various assaults that might maybe adapt to targeted environments and evade detection. Also, attackers are using automation to expedite their operations.
The increasing threats and exposure point out that cyber security is well-known to companies final productive and aggressive, as effectively as compliant with a increasing raft of nationwide, regional and international cyber security and privacy regulations.
Cyber security is mountain climbing the board agenda and corporate precedence listing for a increasing option of companies as enterprise leaders an increasing selection of ticket that they favor to head beyond mere compliance to make certain they’ve the well-known cyber security capabilities to deal with the enterprise operating and deal with records secure. Files protection is crucial to provide protection to mental property and instil belief in workers, companions and customers.
Cyber security an increasing selection of a strategic aim
In response to the altering vulnerabilities and threats, and the elevated favor to invent belief for aggressive advantage, enterprise leaders are making cyber security a strategic aim. There might be now bigger working out that cyber security mustn’t be an afterthought pushed by compliance, however ought to be an integral portion of company organisation and processes if the enterprise is to dwell on and dwell aggressive.
Comprehensive cyber security, which potential truth, desires to be the aim of every winning enterprise, and might maybe also be carried out by following a contemporary cyber security framework or architecture. Cyber security tools are well-known to enabling organisations to provide protection to records, detect malicious project, answer to assaults and get better from them like a flash to minimise the impression on enterprise operations.
It’s additionally crucial to dangle in mind that cyber security is no longer handiest about preserving the enterprise in opposition to explain threats, however the truth is about offering the cyber protections that the enterprise desires to be viable. Cyber security is which potential truth about working with the enterprise to make certain that the enterprise can innovate and enact its aim by guaranteeing a secure IT atmosphere to characteristic in.
In the an identical come that the UK’s Nationwide Cyber Safety Centre is aiming to manufacture the UK a secure situation to achieve enterprise, every enterprise desires to work with its cyber security teams to make certain the organisation’s IT atmosphere is a secure situation to achieve enterprise for personnel, companions and customers.
The cyber security industry is evolving based on altering market requirements by offering current sorts of tools and capabilities. And given the increasing importance of cyber security systems and tools to enterprise, the final cyber security market will continue to adapt and develop in importance, size and stamp.
These sub-sections of the market that enhance digital transformation, including the switch to the cloud, will survey the greatest evolution, investment and enhance, whereas more outmoded security applied sciences have a tendency to experience some decline, especially those centered on on-premise expend conditions and legacy systems.
The role of a cyber security architecture
To attain what applied sciences and capabilities are connected to cyber security, the place they match in, and their major role, organisations favor to attract the systems they already dangle in opposition to a security reference architecture.
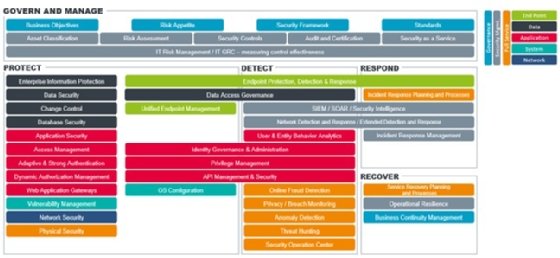
Latest security reference architectures characteristic five well-known building blocks of a comprehensive and effective unique come to cyber security:
- Govern and manage
- Give protection to
- Detect
- Acknowledge
- Enhance
Every of those building blocks entails loads of key parts or capabilities which might maybe well be well-known to enact a appropriate level of cyber security.
In various phrases, cyber security capabilities (applied sciences and processes) tumble into the overarching govern and manage block or one or more of the four pillars of cyber security: provide protection to, detect, answer and get better.
Govern and manage
The govern and manage block entails every thing required for an overarching come to declaring a security architecture and declaring security. The parts in the govern and manage block are connected for all areas of cyber security and invent the unsuitable of the reference architecture.
Interior the govern and manage block, we discover governance aspects similar to enterprise objectives, risk urge for food, security framework and standards, and security administration aspects similar to asset classification, risk assessment, security controls, audit and certification, security as a service, IT risk administration, and IT governance, risk and modify. This block is set using a risk-based come to title risks that ought to be mitigated by using the four various pillars.
A security reference architecture additionally most incessantly references five major abilities “layers”:
- Endpoint
- Files
- Utility
- Gadget
- Community
Further overarching layers are:
- Governance
- Safety administration
- Rotund service
Rotund service highlights those parts that screen all five of the major cyber security layers.
Give protection to, detect, answer, get better
The provide protection to pillar entails every thing that has to achieve with preserving records, including switch controls, catch admission to controls, vulnerability administration, and community and physical security. It additionally entails loads of parts that span one or two various pillars, similar to endpoint protection, detection and response (which additionally spans the detect and answer pillars).
The detect pillar entails every thing connected to detecting threats and anomalous or malicious project. Several parts span one or two various pillars, similar to the SIEM/security intelligence part. The detect pillar additionally entails five “full-service” parts that screen all layers of cyber security, particularly: online fraud detection, privacy/breach monitoring, anomaly detection, threat hunting and security operations centre.
The answer pillar is changing into an increasing selection of crucial as organisations realise they cannot depend handiest on protection applied sciences to deal with cyber attackers out of their corporate networks and must dangle some skill to answer when security breaches attain happen. The answer pillar entails parts which might maybe well be designed to make certain that as soon as an organisation’s cyber defences are breached, the impression of the attack is saved to an absolute minimum. The point of interest of this block is on incident response.
The get better pillar entails parts which might maybe well be designed to make certain that in the match of a cyber attack, classic enterprise processes either continue to whisk or are returned to operation as like a flash as most likely. This most incessantly entails issues indulge in malware removal, roll-relief of nodes to the best identified appropriate say, placing more zero-belief suggestions in areas the place the attack took situation, auditing particular person accounts, resetting or casting off credentials, and identifying security gaps or vulnerabilities that favor to be addressed.
Operational resilience is a key part and but some other an increasing selection of crucial space of focal point in the cyber defence arsenal. Guaranteeing that a enterprise can continue to characteristic and get better like a flash from cyber assaults is well-known to reducing the impression of assaults and guaranteeing the long-term survival of the organisation.
Suggestions
Organisations must verify what security applied sciences and capabilities they’ve and evaluate that with a contemporary cyber security reference architecture, similar to the one described above, to title the gaps.
The next spin is to evaluate by which portray the gaps favor to be stuffed in step with a risk evaluation, followed by drawing up an implementation notion. On this come, organisations can undertake a structured come to cyber security investments that ensures that the greatest risks are addressed as a precedence.
Read more on Safety coverage and particular person consciousness
![]()
The Safety Interviews: How SolarWinds got here by means of its darkest hour

By: Alex Scroxton
![]()
Safety Teach Tank: Zero belief is complex, however has prosperous rewards
![]()
CISOs flip to AI, detection, response and training

By: Warwick Ashford
![]()
Safety Teach Tank: Files architects desires to be key allies of infosec execs

By: Eoin Keary