
Is your VPN salvage? Solutions to originate sense of VPN encryption
You don’t must unexcited be a security educated to ascertain up on your VPN’s marketing claims.

Koldunov / Getty Photos
As of late’s Most efficient Tech Affords
Picked by PCWorld’s Editors
Top Affords On Gargantuan Products
Picked by Techconnect’s Editors
Virtual private networks use slick marketing terms to appeal capacity users, but you likely can without distress earn tousled when attempting to hold it all aside. The language describing encryption suggestions is thick with acronyms and technical jargon, so browsing cute phrases fancy “armed forces-grade encryption” usually turns up extra questions than answers.
However whereas the main points of encryption can before every part be advanced, issues change into magnificent drag while you already know the categorical technique to model out the toddle in the park. Ideas fancy TLS, RSA certificates, keys, AES encryption, and the fancy will seem a long way much less international, and it’ll be a snap to review how great a VPN is of your attention. Right here’s the categorical technique to earn there.
How VPN encryption works
Customarily talking, encryption is the path of of converting records into code (an act identified as encoding), which will then entirely be decoded by an authorized party. When your computer connects to a VPN, a multi-step encryption path of must unexcited happen. The extent of security in every of those steps is reckoning on the protocols ragged. Every protocol handles ingredients fancy authentication, key substitute, and encryption of the established connection in assorted manners.
Which you can usually damage down unique VPN encryption protocols into these four ingredients:
- How the connection first begins (the “handshake”)
- How the connection generates the portion of code (“the main”) ragged to encrypt and decrypt records for the length of the session (aka the main substitute)
- How long the encryption keys persist
- The encryption system ragged to guard the established connection
The protocols supported by a given VPN existing the total stage of encryption power, but they’re going to also be configured to taste. As a end result, VPN providers and products can use the same protocols but provide differing ranges of security. One company could simply hew closer to commercial defaults to boast faster speeds, whereas one other could lengthen the main lengths/sizes ragged for encryption to maximize security.
Solutions to untangle the specifics of VPN encryption
 PCWorld
PCWorldMany VPNs toughen OpenVPN, a preferred commence-source protocol identified for its excessive stage of security.
Birth by determining which protocols a explicit VPN carrier helps. For the time being, the commercial favors three for his or her excessive security: OpenVPN, IKev2/IPSec, and Wireguard. Which you can additionally ogle proprietary riffs on identified protocols, as smartly as slower or much less salvage ones fancy SoftEther, SSTP, and L2TP/IPSec. PPTP is abnormal this display camouflage day, because it’s an outdated protocol and no longer provides sufficient security.
Next, dig up the main points of how the VPN has configured its chosen protocols. Most providers and products provide a nuts-and-bolts clarification in toughen pages, an FAQ, or weblog posts. It is most practical to unexcited stumble on terms fancy “RSA certificates” and “Elliptic Curve Diffie Hellman protocol” here. Online browsing will define any terms you’re now not aware of.
Someway, seize the general jargon that you just’ve stumbled on and weigh it against commercial requirements. All over again, on-line browsing will abet you to love in any knowledge gaps. Be cautious of VPNs that don’t meet unique commercial defaults (e.g., 2048-bit keys for RSA certificates and 128-bit AES encryption). A VPN’s stage of encryption must unexcited line up with its marketing claims, too—a supplier that trumpets the iron-clad security but makes use of PPTP and even L2TP/IPSec presents motive for doubt.
To illustrate, here’s how we would streak about interpreting HotSpot Protect VPN’s clarification of its encryption suggestions:
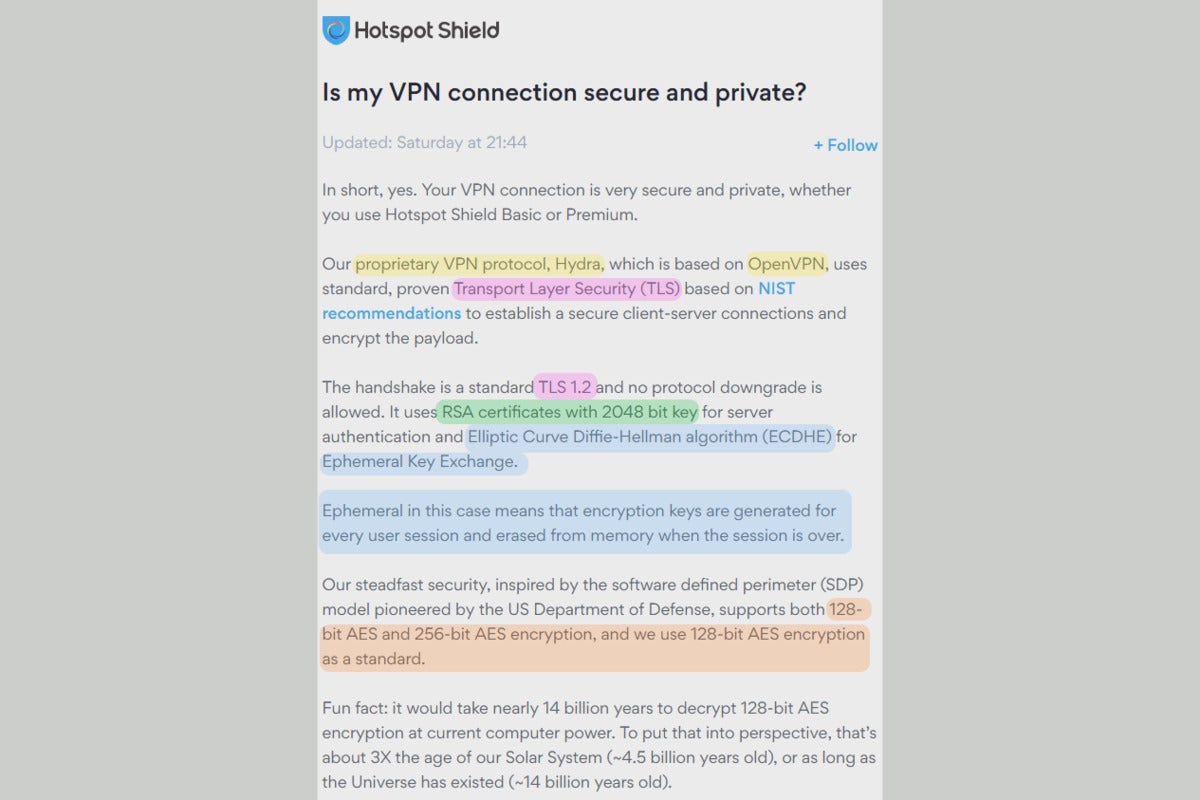 PCWorld
PCWorldOn this clarification of HotSpot Protect’s encryption configuration, the brightly colored highlights are what or now not you will want to work out.
First, we’d identify supported VPN protocols. The critical phrase here is “proprietary protocol in conserving with OpenVPN.” That tells us that this company has taken one amongst the most salvage VPN protocols and build their private high-tail on it. You’ll like to belief that it has applied those changes smartly, for the reason that code is now not publicly on hand to overview. (In distinction, OpenVPN is an commence-source protocol.)
Next, we would puzzle out what purpose the relaxation terms signify accurate throughout the OpenVPN protocol. With a runt of labor, it becomes drag that:
- TLS 1.2 pertains to security on the commence of a connection;
- RSA certificates are share of that encryption path of;
- The Elliptic Curve Diffie Hellman algorithm then dictates how key substitute happens;
- That key substitute is an ephemeral substitute;
- The connection switches over to 128-bit AES encryption in a while. Which you can configure your connection to as an alternative use 256-bit AES encryption.
 PCWorld
PCWorldWikipedia has explanations for many encryption-associated terms, but it undoubtedly could flip into a rabbit gap whereby you utilize gobs of time unpacking the extremely technical language.
To search out out whether or now not or now not HotSpot Protect VPN has made dapper decisions for its setup, extra be taught supplies additional context:
- TLS 1.2: OpenVPN makes use of Transport Layer Security, or TLS, to salvage the connection when it begins. Version 1.2 is thought of the minimum default by consultants. A newer, extra salvage version 1.3 exists as smartly but has now not yet been as broadly adopted.
- RSA certificates with 2048-bit key: TLS certificates depend on the RSA algorithm to aid records transmission salvage. The minimum key dimension advised this display camouflage day is 2048-bit. Some VPNs use a longer key dimension (4096-bit), however the tradeoff is that it’s slower.
- Elliptic Curve Diffie Hellman algorithm: This protocol dictates how the portion of records (the main) ragged to encrypt and decrypt records routed throughout the VPN is generated. Worship the RSA algorithm, ECDH relies on asymmetrical public-private key pairs but has assorted vulnerabilities. Its use following that of RSA certificates helps mitigate those weaknesses.
- Ephemeral key substitute: Recurring keys are generated every session and then discarded, which reduces the probability of a third party obtaining the keys and thus decrypting your records.
- 128-bit AES and 256-bit AES encryption: 256-bit AES encryption is extra advanced than the 128-bit model, which provides extra security against brute-pressure assaults, but it undoubtedly’s also slower. By selecting 128-bit AES encryption because the default for established connections but permitting 256-bit as an now not mandatory configuration, HotSpot Protect holds to commercial requirements whereas unexcited giving users the selection to lengthen their stage of security.
Which you can like to test a VPN to additional test it’s charge your time, but between on-line reports and this be taught, you’ll streak into the path of smartly-urged. (Within the explicit case of HotSpot Protect, we’ve already done the reviewing for you.)
General, having the facility to develop this extra or much less test ensures that you just likely can streak on any VPNs that don’t meet your requirements.
Why so sophisticated?
Deciding on these tiny print aside can seize a whereas, that are greater than most other folks are searching to total. Which you can bypass this work by sticking to identified providers and products that are smartly-identified and advised by many consultants in the field. Now we like our private checklist of VPNs that we’ve reviewed that you just likely can reference, which involves suppliers fancy Mullvad, Windscribe, and HotSpot Protect. Opinions flee rampant on forums and sites fancy Reddit, too.
Mark: Must you purchase something after clicking hyperlinks in our articles, we’re going to have the selection to also simply plan a tiny commission. Read our affiliate hyperlink policy for added tiny print.