
Microsoft Replace Server exploits are being targeted by “at the very least 10 hacker groups”
A scorching potato: Four zero-day exploits in Microsoft Replace are being targeted by at the very least 10 superior chronic threat (APT) hacker groups, with net shell backdoors – which allow a long way off administration of a server by task of a net browser – being installed on some 5,000 servers spanning 115 varied international locations.
Four exploits in Microsoft Replace Server hit the news closing week, when we heard that a Chinese hacking neighborhood had targeted the email servers of some 30,000 U.S. govt and industrial organizations. The exploits had been patched by Microsoft, nonetheless the hacking neighborhood identified as “Hafnium” had doubled-up on efforts targeting unpatched servers.
Safety analysis agency ESET has stumbled on that at the very least 10 APT groups are taking profit of the exploits in an strive to compromise servers around the field. Winniti Community, Calypso, Tick, and extra are among the many groups identified.
The protection agency provides that “for the previous few days, ESET researchers were monitoring closely the resolution of net shell detections for these exploits. At the date of newsletter, we had observed extra than 5,000 irregular servers in over 115 international locations where net shells were flagged.” By the spend of the Replace Server exploits to install net shells, hackers can value a long way off administration of a server by task of a net browser.
Share of webshell detections by country (2021-02-28 to 2021-03-09)
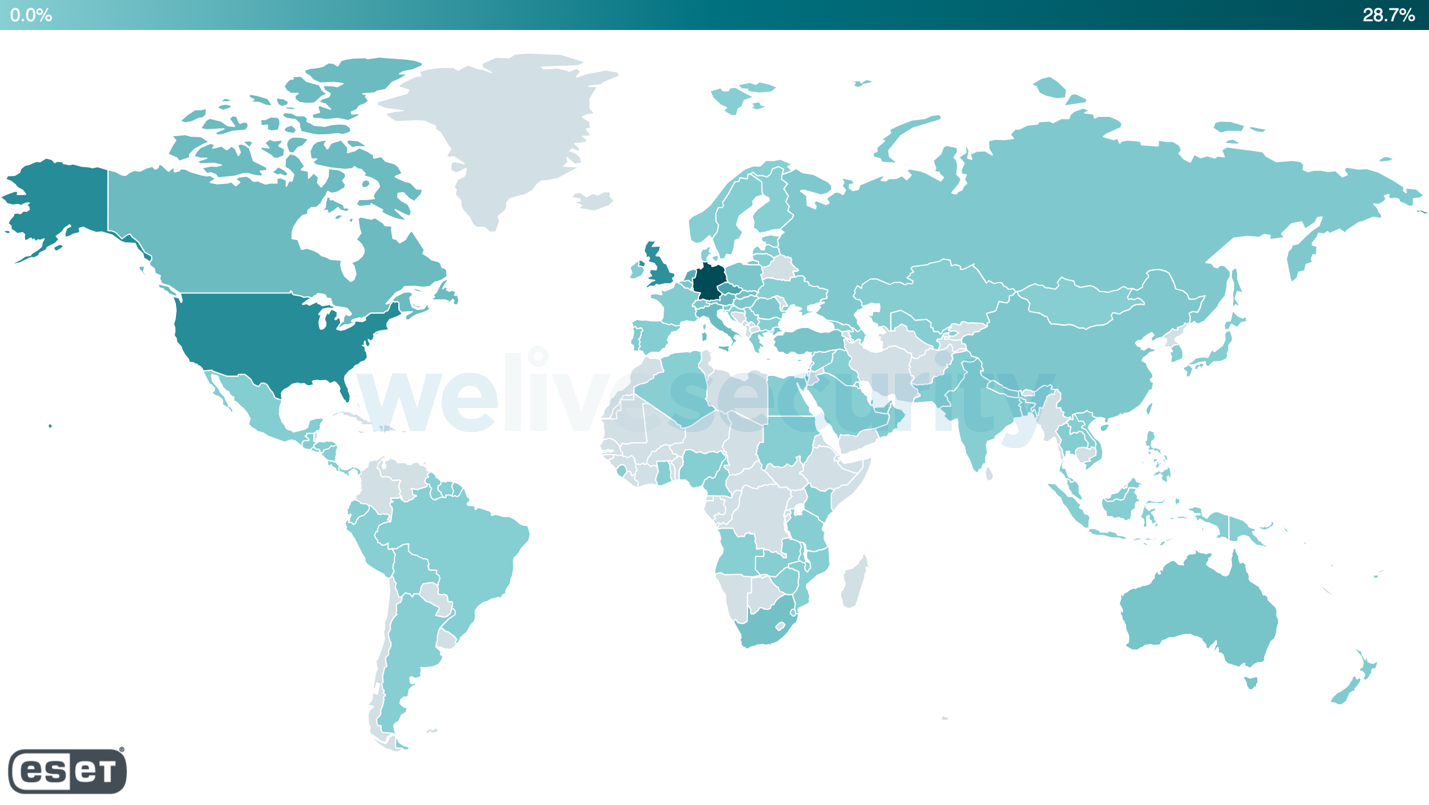
Adopted by that file, ransomware exercise has moreover been detected as hackers strive to recall profit of the slow patching on Replace servers, with assault rates “doubling every few hours.” A ransomware known as ‘DearCry’ is encrypting email on unpatched Replace servers to later quiz cost from the victims for releasing the information.
Microsoft Defender customers the spend of automatic updates fracture no longer want to recall extra action to glean these protections. On-premises Replace Server customers ought to silent prioritize the safety updates outlined right here: https://t.co/DL1XWnitYO
— Microsoft Safety Intelligence (@MsftSecIntel) March 12, 2021
The bottom line? Organizations ought to silent patch their servers the spend of Microsoft’s update as a matter of urgency, before carefully checking logs to walk searching for whether or no longer net shells like already been installed.
To extra safeguard servers, organizations are urged to restrict network rep admission to to users (by task of a VPN, for instance). This ought to silent offer protection to servers from both the current exploits, and any future ones which inevitably prick up in the years to come aid.