
New BrakTooth Bluetooth vulnerabilities bask in an ticket on billions of devices all around the enviornment
Why it matters: Over the last couple of years, now we bask in written about a entire lot of Bluetooth security flaws revealing the fragility of the magic that enables us to pair devices without wires. Security researchers fair currently learned a recent living of vulnerabilities that will presumably per chance smash, freeze, or desire entire care for watch over over billions of devices, but this time it be no longer about a say with the Bluetooth fashioned itself. As a substitute, that is the implications of poorly-conducted instrument firmware that will or could presumably per chance well moreover merely no longer safe patched within the shut to future.
Now no longer too lengthy within the past, security researchers on the Singapore College of Abilities and Create printed a document on a recent living of security vulnerabilities within the Bluetooth tool stacks of a entire lot of industrial products.
The 16 flaws are collectively referred to as “BrakTooth,” and manufacture a large attack ground of billions of devices all around the enviornment that incorporate chips from popular vendors indulge in Intel, Infineon (Cypress), Silicon Labs, Qualcomm, and others.
There are over 1,400 devices known to bask in one or extra of the flaws, including Microsoft’s Floor E book 3, Floor Computer 3, Floor Skilled 7, Floor Hunch 2, a entire lot of Dell Optiplex desktops and Alienware laptops, a form of Asus and HP ultrabooks, as nicely as phones indulge in the Xperia XZ2, Oppo Reno 5G, and the Pocophone F1. Industrial IoT methods based completely round Espressif Systems’ ESP32 and Qualcomm’s CSR8811 chipsets are moreover affected, as are a diversity of PC and consult with wireless instruments, natty home devices, and automobile infotainment methods.
Researchers are disquieted that some vendors are no longer exactly fascinating to fix all these issues, which could presumably be an admittedly laborious job. That stated, the impact does vary from one instrument to the next, with the worst vulnerability being CVE-2021-28139, as it enables an attacker to speed arbitrary code on the aim instrument. Some devices are best inclined to denial-of-carrier attacks that smash the chipset firmware, or would be introduced correct into a impasse condition that disrupts Bluetooth dialog; alternatively, this will in most cases be solved with a straightforward restart.
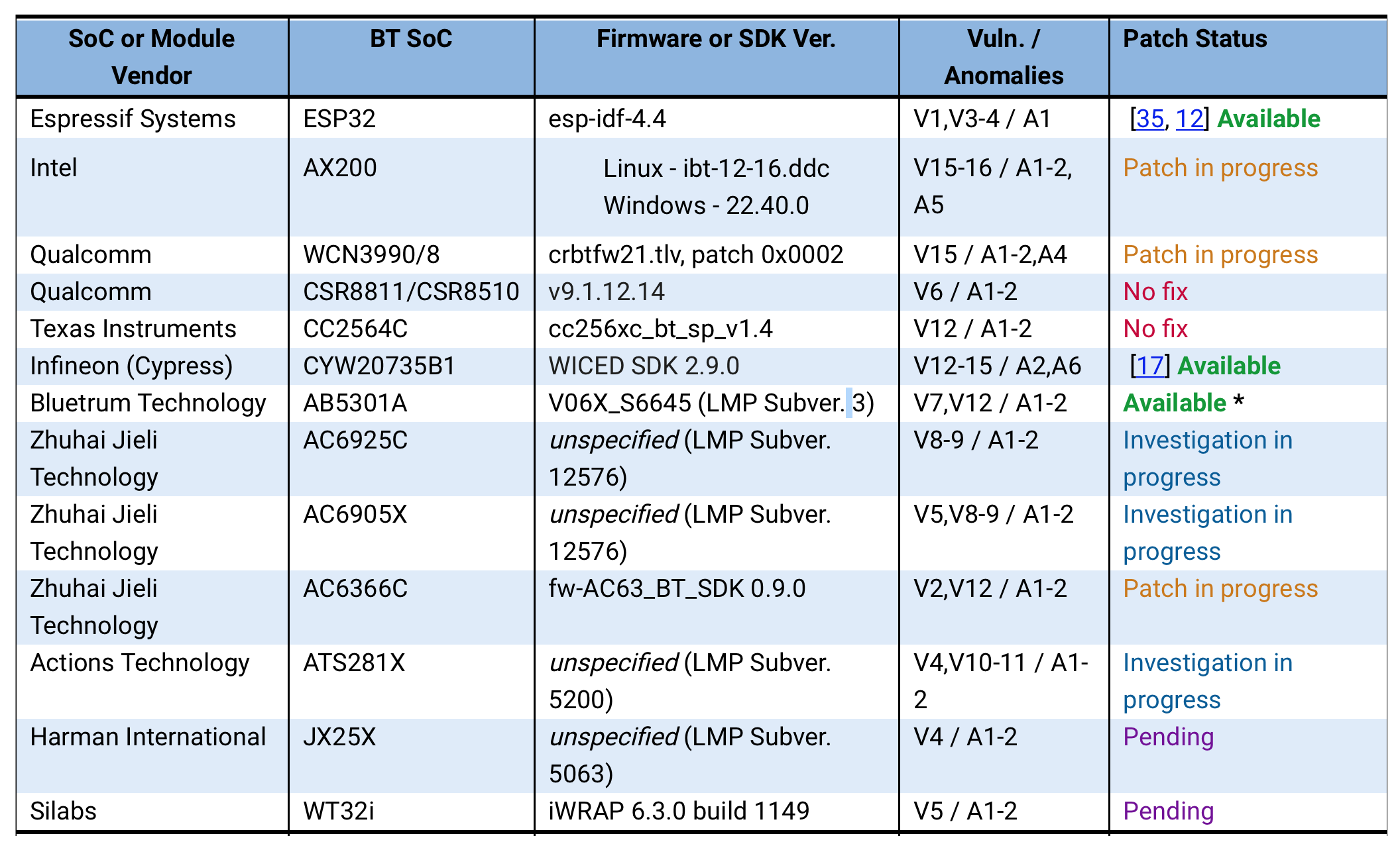
To be definite, the 16 flaws carry out no longer impact the Bluetooth fashioned itself but quite the an expansion of implementations made by chipset vendors. And since extra patches are silent on the arrangement for just a few of the affected devices, researchers bask in delayed the open of their proof-of-design exploits till next month. For an in-depth read on BrakTooth and updates on patching progress, make certain to envision the devoted web set up of living.
As for mitigate the issues, there will not be any longer great you shall be in a region to manufacture besides turning off Bluetooth when no longer in narrate and installing any security updates to your devices as they was on hand.