
Actively exploited macOS 0day let hackers purchase screenshots of contaminated Macs
0DAY NO MORE —
Apple patches vulnerability that malware ancient to bypass macOS privateness protections.

Malicious hackers had been exploiting a vulnerability in absolutely up to this level versions of macOS that allowed them to purchase screenshots on contaminated Macs with out having to salvage permission from victims first.
The zeroday was exploited by XCSSET, a share of malware figured out by security agency Pattern Micro final August. XCSSET ancient what at the time had been two zerodays to contaminate Mac developers with malware that stole browser cookies and recordsdata; injected backdoors into websites; stole recordsdata from Skype, Telegram, and a form of installed apps; took screenshots; and encrypted recordsdata and confirmed a ransom gift.
A third zeroday
Infections got here in the create of malicious initiatives that the attacker wrote for Xcode, a utility that Apple makes on hand for free to developers writing apps for macOS or a form of Apple OSes. As quickly as one amongst the XCSSET initiatives was opened and constructed, TrendMicro talked about, the malicious code would speed on the developers’ Macs. An Xcode venture is a repository for the total recordsdata, sources, and knowledge wanted to assemble an app.
In March, researchers from SentinelOne figured out a recent a trojanized code library in the wild that also installed the XCSSET surveillance malware on developer Macs.
On Monday, researchers with Jamf, a security provider for Apple venture users, talked about that XCSSET has been exploiting a zeroday that had long gone undetected till recently. The vulnerability resided in the Transparency Consent and Regulate framework, which requires explicit user permission before an installed app can invent system permissions to entry the onerous force, microphone, camera, and a form of privateness- and security-shapely sources.
XCSSET had been exploiting the vulnerability so it might perhaps well presumably bypass TCC protections and purchase screenshots with out requiring user permission. Apple mounted CVE-2021-30713 (as the vulnerability is tracked) on Monday with the open of macOS 11.4.
The vulnerability was the results of a standard sense error that allowed XCSSET to veil inside the list of an installed app that already had permission to purchase screenshots. The exploit allowed the malware to inherit the screenshot permissions, as smartly as a form of privileges controlled by TCC.
Piggybacking off parent apps
“Some developers create purposes with smaller purposes positioned inside them,” Jamf researcher Jaron Bradley talked about in an interview. “This isn’t out of the ordinary. However a bug appears to be like to have existed in the running system common sense in phrases of how the TCC permissions are dealt with in this sort of region.”
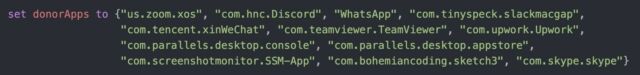
To stumble on apps that XCSSET might perhaps well presumably piggyback off of, the malware checked for screen screen preserve shut permissions from a list of installed purposes.
“As expected, the list of application IDs that are centered are all purposes that users recurrently grant the screen screen sharing permission to as half of its out of the ordinary operation,” Bradley wrote in a put up. “The malware then uses the following mdfind bid—the bid-line-essentially based fully model of Spotlight—to confirm if the appID’s are installed on the victim’s system.”
Jamf
The put up outlined how the float of the AppleScript guilty for the exploit worked:
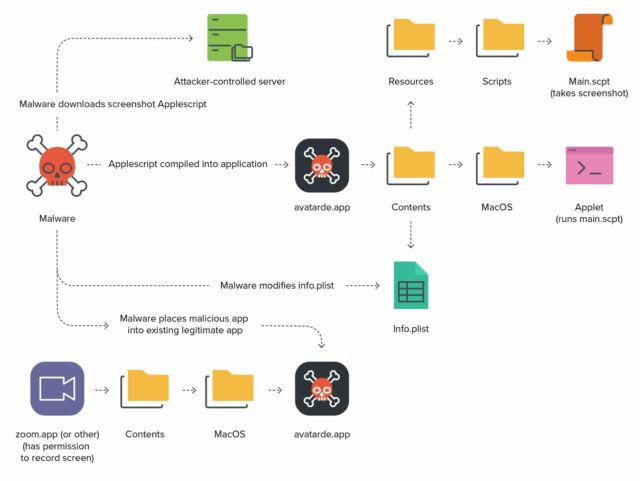
- The XCSSET AppleScript screenshot module is downloaded from the malware writer’s bid and regulate (C2)server (to the ~/Library/Caches/GameKit folder).
- The usage of the osacompile bid, the screenshot module is converted to an AppleScript-essentially based fully application called avatarde.app. When any AppleScript is compiled in this form, an executable called “applet” is positioned in the newly created application bundle’s /Contents/MacOS/ list and the script that the applet will attain will also be positioned at /Contents/Assets/Scripts/main.scpt.
- The newly created Recordsdata.plist is then modified by the plutil binary, changing the want surroundings LSUIElement to moral. This enables the applying to be speed as a background process, concealing its presence from the user.
- A clean icon is then downloaded and utilized to the applying.
- Lastly, the newly created application is positioned inside the already existing donor application the employ of the following code:
As an illustration, if the virtual meeting application zoom.us.app is figured out on the system, the malware will space itself cherish so:
/Capabilities/zoom.us.app/Contents/MacOS/avatarde.app
If the victim computer is running macOS 11 or elevated, this might then signal the avatarde application with an ad-hoc signature, or one that is signed by the pc itself.
As soon as all recordsdata are in space, the custom application will piggyback off of the parent application, which in the example above is Zoom. This implies that the malicious application ought to purchase screenshots or file the screen screen with out desiring explicit consent from the user. It inherits those TCC permissions outright from the Zoom parent app. This represents a substantial privateness anguish for dwell-users.
For the length of Jamf’s attempting out, it was agency that this vulnerability is just not any longer restricted to screen screen recording permissions both. Loads of a form of permissions that have already been supplied to the donor application will also be transferred to the maliciously created app.
Jamf
Now that Apple has mounted the vulnerability, TCC works the scheme in which Apple intended, with a dialog message that prompts users to both commence the system preferences to allow the app or to merely click on the bellow button displayed by the popup.
XCSSET isn’t at likelihood of infect Macs until it has speed a malicious Xcode venture. Which implies folks are no longer at likelihood of be contaminated until they are developers who have ancient one amongst the initiatives. The Jamf put up provides indicators of a compromise list that folks can employ to decide on in the occasion that they’ve been contaminated.