
Ransomware gangs be taught about of us expertise for negotiations

phloxii – STOCK.ADOBE.COM
The approach of negotiating a ransomware price is tranquil, and cyber criminal organisations are ready to give good terms to those with the true skillsets
The increasing sophistication of the cyber criminal underground is now mirrored in how ransomware operations set apart together their crews, in quest of out specialist expertise and skillsets. Indeed, some gangs are coming to resemble corporations, with diversified roles and outsourced negotiations with victims, in step with current analysis printed by Kela, a supplier of threat intelligence services.
Kela analyst Victoria Kivilevich and diversified people of the crew spent over a year monitoring the darkish net cyber job ecosystem, and rapid established the existence of four most well-known areas of specialisation:
- Coding, or procuring malware with wanted capabilities.
- Infecting focused victims.
- Affirming obtain admission to to victim programs, and exfiltrating and processing their knowledge.
- Monetisation, cashing out, selling, or otherwise monetising the stolen knowledge.
Each of those stages involves varied malicious actions where varied expertise would perchance perchance furthermore fair advance in helpful, and Kivilevich acknowledged her crew had discovered that once having a seek particularly at the ransomware provide chain, many actors are concentrating around the extraction enviornment of interest, focusing on escalating their privileges within the compromised community, and the monetisation enviornment of interest, where actors are excited by extracting ransoms at some level of victim negotiations.
Folks with the precise – and no longer necessarily technical – skillsets to establish ransom negotiations are in particular valued, Kela discovered. “We observed more than one posts [on the dark web] describing a current characteristic within the ransomware ecosystem, negotiators, whose reason is to pressure the victim to pay a ransom using insider knowledge and threats,” acknowledged Kivilevich.
“Victims started using negotiators – whereas about a years ago there used to be no such profession, now there might perchance be a quiz for negotiating services. Ransomware-negotiation consultants partner with the insurance corporations and wouldn’t in discovering any lack of customers. Ransom actors needed to up their game as smartly, in uncover to obtain good margins.
“As most ransom actors doubtlessly are no longer native English audio system, more tranquil negotiations – particularly around very high budgets and surrounding advanced enterprise eventualities – required better English. When REvil’s consultant used to be procuring for a ‘make stronger’ member of the crew to defend negotiations, they particularly talked about ‘conversational English’ as one among the calls for. Here is now not any longer a current case: actors are attracted to native English audio system to make use of for spear-phishing campaigns.”
Kivilevich discovered several threads on Russian-talking underground boards where cyber criminals were procuring for negotiators and discussing their work.
Within the image under – which Kela translated from Russian using Google services – a threat actor who has already established persistence on the community of a victim in Saudi Arabia looks to demand an insider, or anyone with contacts, at Middle Eastern cyber security corporations who can hand over contact miniature print for the victim’s IT managers in uncover to conduct negotiations. Remuneration in this case would be between $1m and $5m (£720,000 to £3.6m, or €840,000 to €4.22m), or likely about 20% of the ransom.

And true as a exact organisation would perchance perchance book a contractor who looks to be a detrimental fit, ransomware gangs would perchance perchance furthermore furthermore obtain detrimental hiring decisions, and on some of the boards, Kela discovered proof of disagreements between ransomware gangs and their hired guns (gape picture under).
In a single documented instance, miscommunication between a Conti affiliate and a hired negotiator blew up into an outright dispute within the tried April 2021 extortion of the Broward County Public College District in Florida.
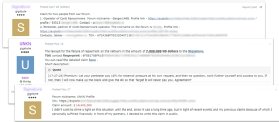
The negotiator claimed that they had insider knowledge that would perchance perchance pressure the victim to pay up – they had demanded $40m, in itself a giant overreach – but then accused Conti’s affiliate of meddling within the negotiations and operating their efforts. Conti countered by accusing the negotiators of behaving unprofessionally.
Others then weighed in on the forum with their experiences, with a consultant of REvil – currently at the centre of the unfolding Kaseya incident – accusing the negotiator of being a scammer.
Kela’s anecdote goes into more declare about some of the specialist roles ransomware operators are ready to pay colossal bucks for, equivalent to obtain admission to brokers, intrusion consultants (or penetration testers), and owners of botnets for connected distributed denial of carrier (DDoS) assaults. It would also be read in stout here.
Squawk material Continues Beneath

Be taught more on Hackers and cybercrime prevention
![]()
REvil affiliates offer hefty ransom discounts, knowledge reveals

By: Valéry Marchive
![]()
NCSC CEO: UK-Eire collaboration most well-known to quit cyber threats

By: Alex Scroxton
![]()
Unit 42 warns of emergent Prometheus ransomware

By: Alex Scroxton
![]()
ExaGrid published as latest Conti ransomware casualty

By: Shaun Nichols



