
Researcher says he can link Facebook accounts to 5M electronic mail addresses per day
VIDEO DEMO —
Facebook Electronic mail Search v1.0 can course of 5 million electronic mail addresses per day, researcher says.

Level-headed smarting from final month’s dump of cell phone numbers belonging to 500 million Facebook users, the social media wide has a fresh privacy disaster to contend with: a software that, on a mass scale, links the Facebook accounts associated with electronic mail addresses, even when users opt settings to defend them from being public.
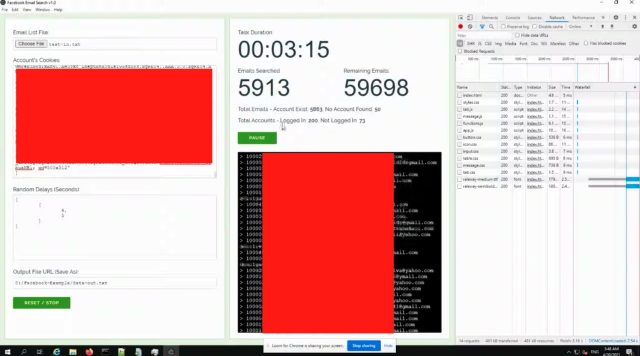
A video circulating on Tuesday showed a researcher demonstrating a software named Facebook Electronic mail Search v1.0, which he said might per chance well per chance presumably also link Facebook accounts to as many as 5 million electronic mail addresses per day. The researcher—who said he went public after Facebook said it did no longer judge the weakness he learned used to be “crucial” ample to be fixed—fed the software a list of 65,000 electronic mail addresses and watched what took place next.
“As that you simply might per chance also stumble on from the output log right here, I’m getting a fundamental amount of outcomes from them,” the researcher said because the video showed the software crunching the address list. “I’ve spent per chance $10 to elevate 200-queer Facebook accounts. And within three minutes, I if fact be told comprise managed to carry out this for six,000 [email] accounts.”
Ars acquired the video on condition the video no longer be shared. A fleshy audio transcript seems to be on the tip of this put up.
Losing the ball
In a assertion, Facebook said: “It seems to be that we erroneously closed out this worm bounty story earlier than routing to the appropriate workers. We fancy the researcher sharing the positive wager and are taking initial actions to mitigate this distress while we be conscious up to higher perceive their findings.”
A Facebook handbook did no longer acknowledge to a ask asking if the firm told the researcher it did no longer comprise in mind the vulnerability crucial ample to warrant a fix. The handbook said Facebook engineers accept as true with they’ve mitigated the leak by disabling the strategy shown within the video.
The researcher, whom Ars agreed no longer to name, said that Facebook Electronic mail Search exploited a front-discontinue vulnerability that he reported to Facebook no longer too long within the past however that “they [Facebook] carry out no longer accept as true with to be crucial ample to be patched.” Earlier this 365 days, Facebook had a same vulnerability that used to be sooner or later fixed.
“Here’s in actuality the categorical same vulnerability,” the researcher says. “And for some reason, despite me demonstrating this to Facebook and making them conscious of it, they’ve told me staunch now that they won’t be taking action towards it.”
On Twitter
Facebook has been under fire no longer appropriate for offering the strategy for these big collections of information, however additionally the blueprint it actively tries to promote the muse they pose minimal hurt to Facebook users. An electronic mail Facebook inadvertently sent to a reporter on the Dutch publication DataNews suggested public family members folks to “frame this as a astronomical industry distress and normalize the proven fact that this job happens regularly.” Facebook has additionally made the honor between scraping and hacks or breaches.
It’s no longer certain if any individual actively exploited this worm to assemble a huge database, however it completely would no longer be soft. “I accept as true with this to be moderately a deadly vulnerability, and I’d fancy reduction in getting this stopped,” the researcher said.
Here is the written transcript of the video:
So, what I’d fancy to provide a proof for right here is an brisk vulnerability within Facebook, which lets in malicious users to search info from, um, electronic mail addresses within Facebook and comprise Facebook return, any matching users.
Um, this works with a front discontinue vulnerability with Facebook, which I’ve reported to them, made them conscious of, um, that they carry out no longer accept as true with to be crucial ample to be patched, uh, which I’d accept as true with to be moderately a fundamental, uh, privacy violation and a wide venture.
This kind is currently being ancient by software, which is on hand fair now all over the hacking neighborhood.
At the moment or no longer it’s being ancient to compromise Facebook accounts for the rationale for taking on pages groups and, uh, Facebook selling accounts for clearly financial attach. Um, I’ve location up this visible example within no JS.
What I’ve completed right here is I’ve taken, uh, 250 Facebook accounts, newly registered Facebook accounts, which I’ve purchased online for about $10.
Um, I if fact be told comprise queried or I’m querying 65,000 electronic mail addresses. And as that you simply might per chance also stumble on from the output log right here, I’m getting a fundamental amount of outcomes from them.
If I if fact be told comprise a stumble on on the output file, that you simply might per chance also stumble on I if fact be told comprise a person ID name and the e-mail address matching the enter electronic mail addresses, which I if fact be told comprise ancient. Now I if fact be told comprise, as I thunder, I’ve spent per chance $10 utilizing two to elevate 200-queer Facebook accounts. And within three minutes, I if fact be told comprise managed to carry out this for six,000 accounts.
I if fact be told comprise examined this at a increased scale, and it’s that you simply might per chance also judge of to utilize this to extract feasibly up to 5 million electronic mail addresses per day.
Now there used to be an present vulnerability with Facebook, uh, earlier this 365 days, which used to be patched. Here’s in actuality the categorical same vulnerability. And for some reason, despite me demonstrating this to Facebook and making them conscious of it, um, they’ve told me staunch now that they won’t be taking action towards it.
So I’m reaching out to folks equivalent to yourselves, uh, in hope that you simply might per chance also use your affect or contacts to gain this stopped, as a outcome of I’m very, very assured.
Here’s no longer easiest an astronomical privacy breach, however this might per chance well also discontinue up in a fresh, one other monumental data dump, including emails, which goes to allow undesirable occasions, no longer easiest to comprise this, uh, electronic mail to person ID fits, however to append the e-mail address to cell phone numbers, which comprise been on hand in earlier breaches, um, I’m moderately contented to provide a proof for the front discontinue vulnerability so that you simply might per chance also stumble on how this works.
I’m no longer going to level to it on this video merely as a outcome of I originate no longer need the video to be, um, I originate no longer need the model to be exploited, however if I’d be moderately contented to, to provide a proof for it, um, if that is serious, however as that you simply might per chance also stumble on, that you simply might per chance also stumble on continues to output extra and extra and extra. I accept as true with this to be moderately a deadly vulnerability and I’d fancy reduction in getting this stopped.