
Train of the Application Supply Chain 2021
2021
Now in its seventh year, Sonatype’s 2021 Train of the Application Supply Chain Narrative blends a mountainous location of public and proprietary files to repeat fundamental findings about open provide and its increasingly extra fundamental role in digital innovation.

1
Originate Source Supply, Quiz, and Safety
Originate provide provide is increasing exponentially.
At this time, the tip four open provide ecosystems possess a blended 37,451,682 formula and programs. These related communities launched a blended 6,302,733 aloof variations of formula / programs over the past year and have launched 723,570 model aloof projects in red meat up of 27 million builders worldwide.
On hand Supply of Originate Source
Expand in Downloads
300 and sixty five days Over 300 and sixty five days 2020 – 2021
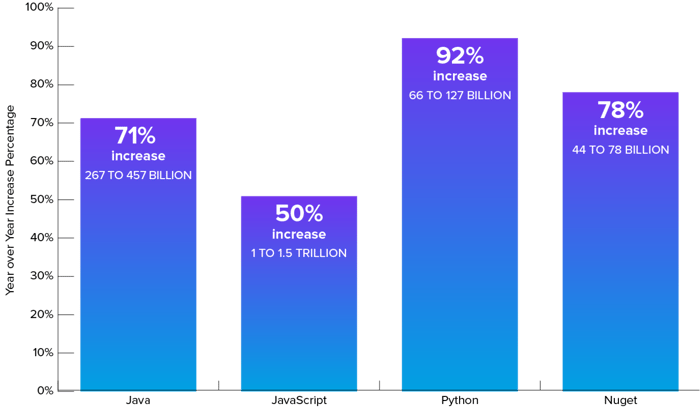
Originate provide quiz of continues to blow up.
In 2021, builders around the realm will quiz of higher than 2.2 trillion open provide programs, representing a 73% YoY growth in developer downloads of open provide formula. Despite the increasing quantity of downloads, the percentage of accessible formula utilized in manufacturing applications is shockingly low.
Vulnerabilities are extra total in standard projects.
The head 10% of most smartly-liked OSS project variations are 29% likely on moderate to possess identified vulnerabilities. Conversely, the superb 90% of project variations are simplest 6.5% at risk of possess identified vulnerabilities. In aggregate, these statistics point to that the massive majority of security overview (whitehat and blackhat) is centered on finding and fixing (or exploiting) vulnerabilities in projects which will likely be extra many times utilized.
Vulnerability Liberate Density Vs. Repute
2021 Application Supply Chain Statistics
Ecosystem
Total Projects
Total Mission Variations
Procure Requests
300 and sixty five days-Over-300 and sixty five days Procure Mumble
Ecosystem Mission Utilization
Vuln Density for Utilized Variations:
10% Most Smartly-liked
Vuln Density for Utilized Variations:
90% Least Smartly-liked
Java
JavaScript
Python
.NET
Totals/Averages
Excessive-Profile Application Supply Chain Attacks
Dec 2020-July 2021
DECEMBER 2020
SolarWinds
Risk actors received safe admission to to SolarWinds dev infrastructure, and injected malicious code into Orion change binaries. 18,000 clients robotically pulled trojanized updates, planting backdoors into their methods and allowing unsuitable actors to consume non-public networks at will.
FEBRUARY 2021
Namespace Confusion
Three days after news broke of an ethical researcher hacking over 35 noteworthy tech corporations in a fresh provide-chain attack, higher than 300 malicious copycat assaults were recorded. Inner one month, higher than 10,000 namespace confusion copycats had infiltrated npm and utterly different ecosystems.
APRIL 2021
Codecov
An attacker became once ready to safe safe admission to to a credential by skill of a mistake in how Codecov were constructing Docker pictures. This credential then let them regulate Codecov’s bash uploader script which became once both used straight by clients or by skill of Codecov’s utterly different uploaders esteem their Github Motion. The attacker used this modified script to steal credentials from the CI environments of clients the utilization of it.
MAY 2021
Microsoft’s WinGet
The weekend after launching, WinGet’s system registry became once flooded with pull requests for apps that were both duplicates or malformed. Some newly added reproduction programs were corrupted and ended up overwriting the present programs, raising serious concerns about the integrity of the WinGet ecosystem.
JULY 2021
Kaseya
A ransomware community came upon and exploited a nil-day vulnerability in monitoring and management system platform used by dozens of managed security suppliers (MSP). On story of these MSPs service hundreds of downstream clients, the hackers were ready to conduct a ransomware attack towards 1,500 victims.
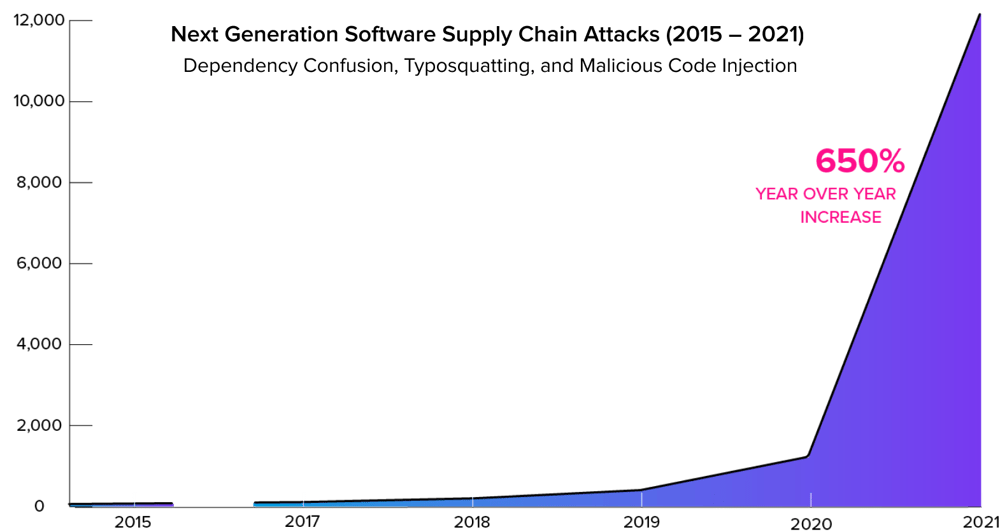
Application Supply Chain Attacks Expand 650%
Contributors of the realm’s open provide community are dealing with a fresh and fleet increasing risk that has nothing to retain out with passive adversaries exploiting identified vulnerabilities in the wild — and all the things to retain out with aggressive attackers deliberately tampering with open provide projects to infiltrate the business system provide chain.
From February 2015 to June 2019, 216 system provide chain assaults were recorded. Then, from July 2019 to May well maybe simply 2020, the series of assaults elevated to 929 assaults. Nonetheless, previously year, such assaults numbered higher than 12,000 and represented a 650% year over year enlarge.
Helpful Recommendation
To tempo up the tempo of digital innovation without sacrificing quality or security, engineering and risk management leaders can even aloof model provide, quiz of, and risk dynamics associated with third-birthday celebration open provide ecosystems. Furthermore, they are going to also aloof slightly elaborate and robotically put into effect open provide policies across every allotment of the souftware provide chain.
2
Thought Exemplary Originate Source Projects
Some open provide projects are actually better than others. But how elevate out you know? This year we examined three utterly different suggestions for figuring out exemplary open provide projects: Sonatype Mean Time to Change (MTTU), OpenSSF Criticality. and Libraries.io Sourcerank. We found that MTTU blended with OpenSSF Criticality are strongly associated with exemplary project outcomes in the areas of security and dev productivity.
Metrics to Use to Assess Relative Quality of an OSS Mission
- Sonatype MTTU
- OpenSSF Criticality
- Libraries.io Sourcerank
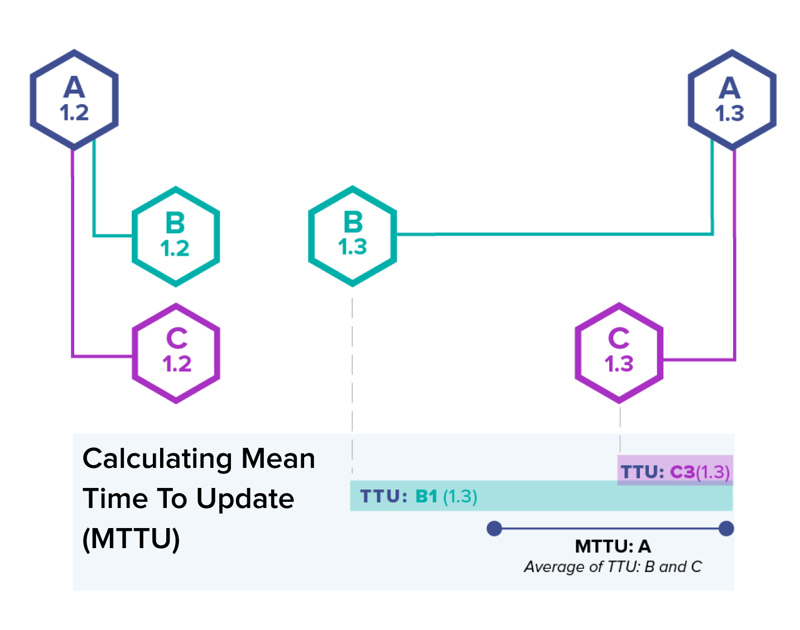
Sonatype MTTU provides a measure of project quality that is essentially based on how fleet the project moves to interchange dependencies. Lower (sooner) is extra healthy. Parts that constantly react fleet to dependency upgrades can have decrease MTTU. Parts that react slowly or have excessive variance of their change times can have elevated MTTU.
OpenSSF Criticality measures a project’s community, utilization, and insist. Right here is distilled into a rating that is intended to measure how fundamental the project is in the open provide ecosystem.
Libraries.io Sourcerank objectives to measure the everyday of system, mostly focusing on project documentation, maturity, and community. It is computed by evaluating a series of certain/no responses comparable to “Is the project higher than six months used?” and a location of numerical questions, comparable to “How many ‘stars’ does the project have?” These are distilled into a single rating, with certain/no questions adding or subtracting a mounted series of “parts” and numerical questions being converted into parts the utilization of a formula, e.g. “log(num_stars)/2.” Essentially the most fresh most series of parts is roughly 30.
Lower MTTU is extra healthy.
Parts that constantly react fleet to dependency upgrades can have low MTTU. Parts that both constantly react slowly or have excessive variance of their response time can have elevated MTTU.
Thunder now we have a ingredient A with dependencies B and C, each and each at version 1.2. Thunder B and C each and each commence a brand aloof version (1.3) and a whereas later A releases a brand aloof version that bumps the version of B and C to 1.3. The time between the commence of B version 1.3 and the commence of A version 1.3 is the Time To Beef up (TTU) for A’s migration to B version 1.3 (and in the same scheme for A’s adoption of C version 1.3). The everyday of all these enhance times is then the MTTU.
Expand for extra perception.
Combination MTTUs are making improvements to over time.
To boot to to the series of projects increasing over the years, there has been a clear trend toward sooner MTTUs. The everyday MTTU across projects in 2011 became once 371 days. In 2014 it became once 302 days and by 2018 it became once 158 days. In 2021, as of August 1, moderate MTTU became once 28 days – much less half of of the 73 days the moderate project took in 2020.
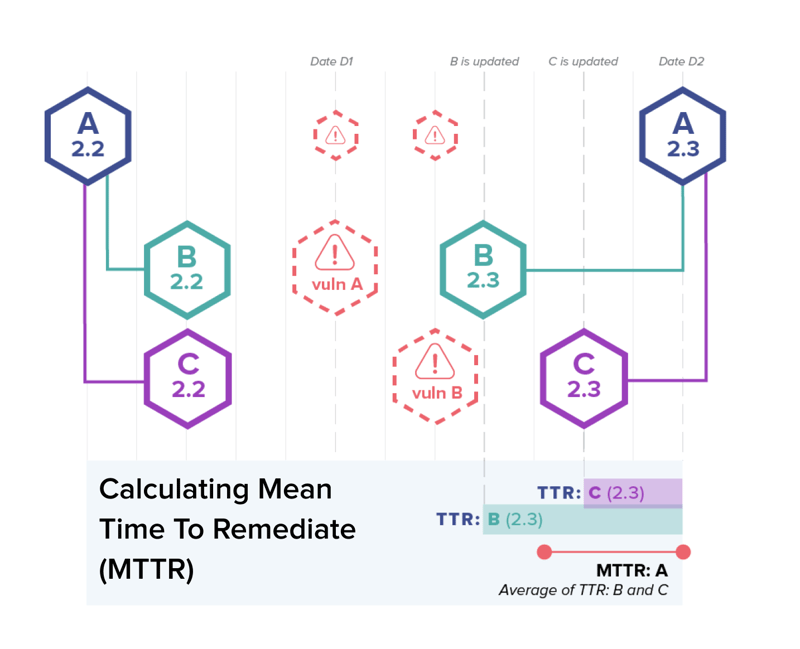
Thunder a project A entails a dependency B, and B has a vulnerability disclosed at date D1. Then A updates the version of B it’s the utilization of on date D2. Time to Remediate (TTR) is then the time between D1 and D2 measured in days, and MTTR is the moderate TTR for a project across all disclosed security vulnerabilities.
Expand for extra perception.
MTTU is extremely correlated to MTTR.
While MTTU would not straight measure the tempo at which projects repair publicly disclosed vulnerabilities, it does correlate to a project’s Mean Time to Remediate (MTTR), which is the time required to interchange dependencies which have printed vulnerabilities. Thus, we decide into story MTTU to be the greatest metric accessible to resolve the impact a ingredient can have on the safety of projects that incorporate it.
Helpful Solutions
Deciding on high quality open provide projects can even aloof be belief to be a fundamental strategic resolution for endeavor system growth organizations.
To steer clear of archaic dependencies and decrease security risks associated with third birthday celebration open provide, system engineering teams can even aloof actively embody projects that constantly narrate low mean time to interchange (MTTU) values and excessive OpenSSF Criticality rankings.
3
How elevate out your pals put together open
provide dependencies?
For this year’s checklist, we examined 4 million precise-world dependency management decisions spread across 100,000 applications. Our learnings highlighted below are enlightening.
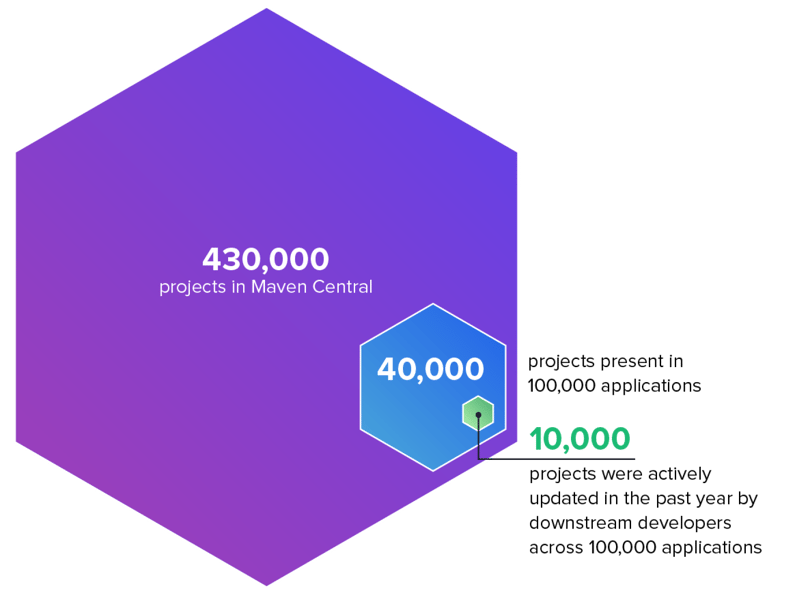
Despite the increasing quantity of downloads, the percentage of accessible formula noticed in manufacturing applications is shockingly low.
On moderate, manufacturing endeavor Java applications insist 10% of accessible open provide formula, and business engineering teams actively change simplest 25% of these formula which will likely be utilized.
Full of life Projects in the Maven Central Repository
5 Groups of Migration Choices
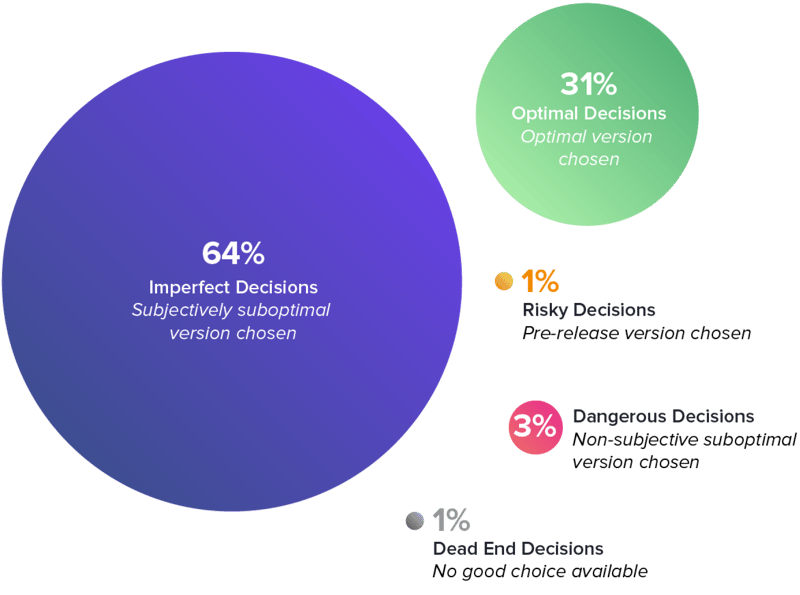
69% of dependency management decisions are suboptimal.
The everyday aloof software program comprises 128 open provide dependencies, and the moderate open provide project releases 10 times per year. This actuality blended with the truth that a pair of hyper active projects commence higher than 8,000 times per year, creates a wretchedness in which builders must constantly judge when (and when no longer to) change third-birthday celebration dependencies within their applications. In gentle of these conditions, Sonatype researchers location out to answer to the query: are builders making atmosphere pleasant dependency management decisions? We studied 100,000 applications and analyzed higher than 4,000,000 ingredient migrations (upgrades) and found that 69% of such decisions were suboptimal.
Despite unstructured resolution making, there might maybe be proof of files in the group.
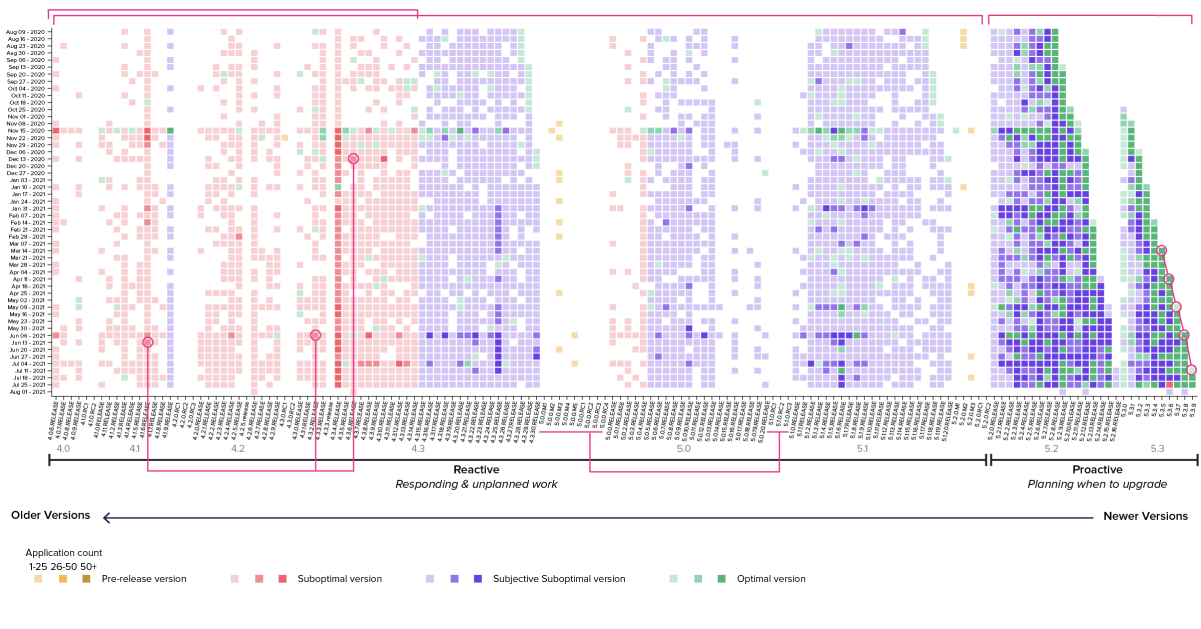
The chart below provides a visual summary of herd migration habits over the past year associated with spring-core, a single ingredient within the extremely standard spring-framework. The y-axis reveals the past 52 weeks of enhance insist, with the tip row representing herd migration decisions made 300 and sixty five days previously, and the bottom row representing herd migration decisions made at some stage in the most most up-to-date week. The x-axis represents the 150 most most up-to-date variations with older variations to the left, and more fresh variations to the supreme. Test key observations by clicking on the dots below.
Herd Migration Behavior of org.springframework:spring-coreAugust 9, 2020–August 1, 2021
1
Essentially the most most up-to-date commence (5.3.x) of spring-core releases roughly every 4 weeks.
2
The project is actively affirming these 2 releases. Darker shading indicates the bulk of the community is the utilization of these releases.
3
The project is never any longer any longer actively supporting these releases. Groups can even aloof migrate away from these archaic variations.
4
Laggards proceed to interchange to older, unsupported, and even susceptible variations.
5
Older variations are susceptible, and older non susceptible variations (4.3.15+) will inevitably be topic to aloof vulnerability disclosures.
6
The community on the total avoids .0 releases and pre-releases.
8 Principles for Upgrading to the Optimal Model
Steer clear of Objectively Inferior Selections

Don’t possess an alpha, beta, milestone, commence candidate, etc. version.
.png?width=68&height=88&name=Vector%20(1).png)
Don’t enhance to a susceptible version.
![]()
Beef up to a decrease risk severity if your most up-to-date version is susceptible.
.png?width=83&height=61&name=Vector%20(3).png)
When a ingredient is printed twice in finish succession, possess the later version.
Steer clear of Subjectively Inferior Selections
.png?width=71&height=96&name=Vector%20(4).png)
Recall a migration path (from version to version) others have chosen.
.png?width=69&height=82&name=Vector%20(5).png)
Recall a version that minimizes breaking code changes.
.png?width=79&height=74&name=Vector%20(6).png)
Recall a version that most of inhabitants is the utilization of.
.png?width=80&height=80&name=Vector%20(7).png)
If all else is tied, possess the most up-to-date version.
Passing these principles finally ends up in optimum upgrades.
Place cash and time.
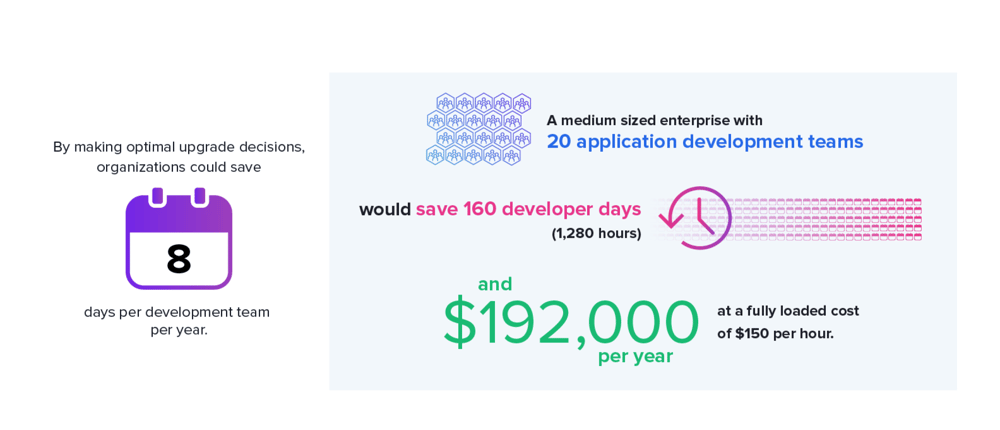
Colorful automation that standardizes engineering teams on exemplary open provide projects can even steal 1.6M hours and $240M of precise world wreck spread across our sample of 100,000 manufacturing applications. Extrapolated out to the total system commerce, the associated financial savings would be billions.
The Just correct thing about Colorful Automation to Dev Groups
Programs for optimum dependency management: reach the sting is most effective.
The bleeding edge is poor. The reach edge is optimum. When analyzing herd migration habits round dependency management practices, we noticed three certain patterns of team of workers habits: Groups residing in dissaray, teams residing on the sting, and teams residing finish to the sting.
Programs for Dependency Administration
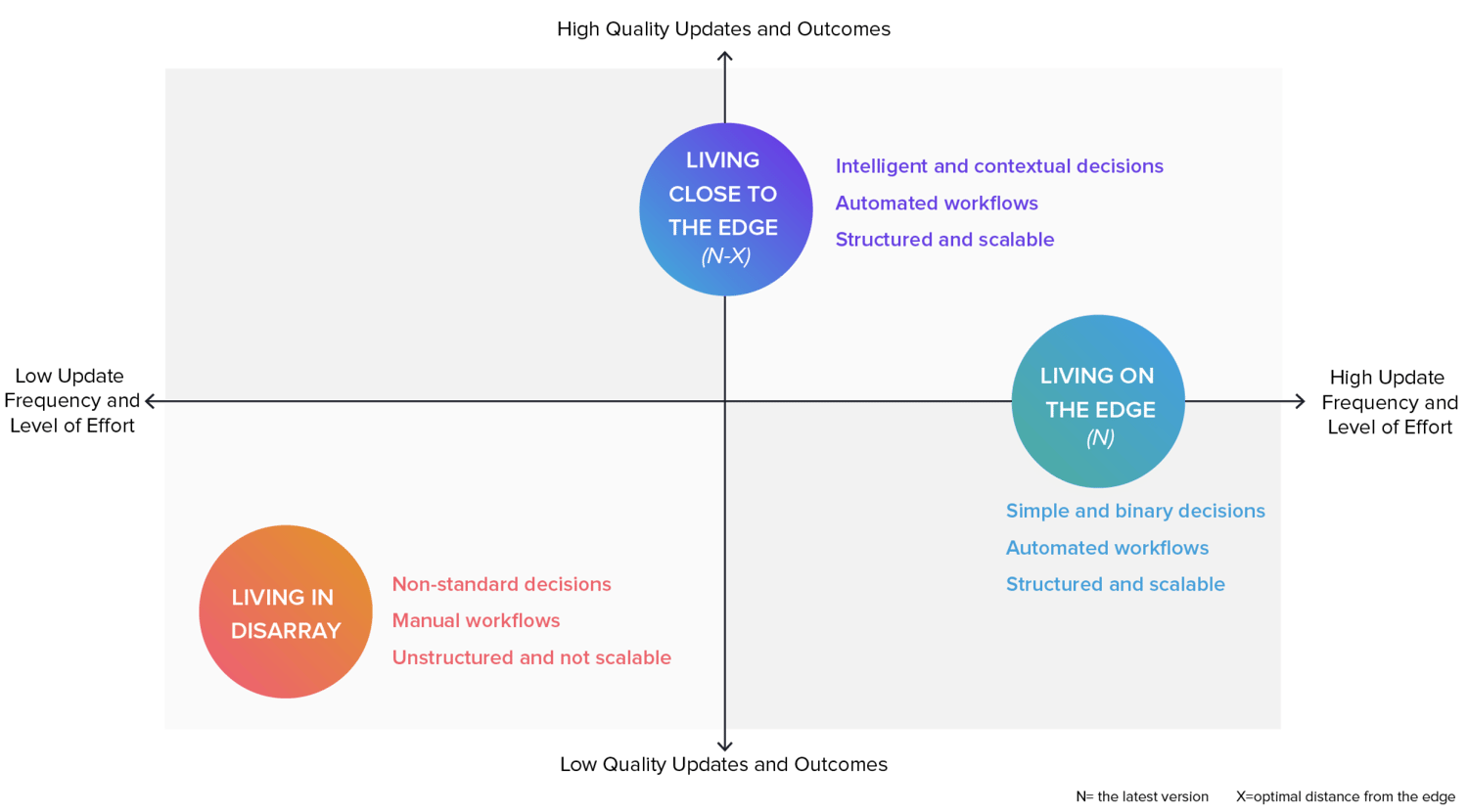
Groups residing in disarray
Builders engaged on these teams lack automatic guidance. They change dependencies on occasion. After they invent out change dependencies, they insist gut instincts and a lot of times have suboptimal decisions. This methodology to dependency management is extremely reactive, no longer scalable, and outcomes in archaic system and elevated security risk.
READ MORE
READ LESS
Groups residing finish to the sting
Builders engaged on these teams have the lend a hand of intellectual and contextual automation. Dependencies are robotically immediate for updating, but simplest when optimum. This scheme of intellectual automation retains system new without inadvertently introducing wasted effort or elevated security risks. This methodology is proactive, scalable, and optimum on the subject of rate effectivity and quality outcomes.
READ MORE
READ LESS
Groups residing on the sting
Builders engaged on these teams have the lend a hand of simplistic, but non contextual, automation. Dependencies are robotically up-to-the-minute to the most up-to-date version, whether or no longer optimum or no longer. Such automation helps to retain system new, but it surely can inadvertently lead to elevated security risks and elevated fees associated with pointless updates and damaged builds. This methodology is proactive and scalable, but no longer optimum on the subject of fees or outcomes.
READ MORE
READ LESS
Helpful Solutions
Application engineering teams can even aloof try to standardize dependency management decisions.
Engineering leaders can even aloof maximize files accessible to builders to construct cash and time.
Engineering leaders can even aloof embody instruments to automate intellectual dependency management decisions.
4
Application Supply Chain Maturity Glimpse
For this year’s checklist, we surveyed 702 engineering professionals about system provide chain management practices, including approaches and philosophies to utilizing open provide formula, organizational assemble, governance, approval processes, and tooling.
Disconnect Between Thought vs Actuality on Application Supply Chain Maturity
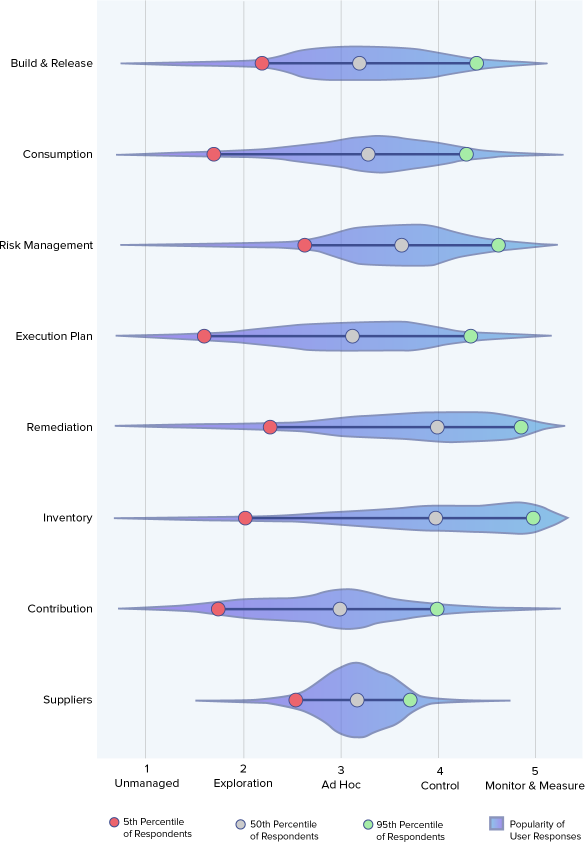
Subjectively, survey respondents checklist they are doing a staunch job remediating notorious formula and point to that they model where provide chain risk resides. Objectively, overview reveals growth teams lack structured guidance and in most cases have suboptimal decisions with admire to system provide chain management.
We plotted all survey responses towards the 5 utterly different levels of system provide chain maturity and found that most of respondents were graded lower than the “Desire a watch on” degree – which is deemed the purpose at which an organization transitions from “figuring it out” to a minimal degree of maturity that can allow high quality outcomes.
Click on the dots to the supreme for additonal insights.
Application Supply Chain Maturity Rating by Theme
fifth, 50th, and 95th Percentile
1
Nearly all of respondents narrate an “Ad Hoc” methodology to system provide chain management
2
The very top two topics where the respondents demonstrated a excessive degree of maturity were for Inventory and Remediation.
3
Comparing survey responses to the aim diagnosis done, we uncover out a pair of disconnect between what’s in total taking place, and what participants mediate goes on: 70% of remediations are genuinely suboptimal.
Helpful Recommendation
The survey suggests that respondents have talked themselves into believing they’re doing a staunch job in areas we uncover out about objectively they set apart no longer seem like. Right here is a reminder to consider of what you deem your organization is doing, versus what’s genuinely taking place and constantly measure your workflow and methods towards desired outcomes.
5
Emergence of Application Supply Chain Law and Requirements
Following several assaults in 2020 aimed at fundamental infrastructure, governments around the realm started to pursue rules and standards aimed at making improvements to system provide chain security and hygiene.

The United States
In May well maybe simply 2021, President Biden signed the Government Mumble on Bettering the Nation’s Cybersecurity, which has been heralded as a milestone for the U.S. government at a time when cyber espionage and nation-reveal assaults on fundamental infrastructure are reaching disaster proportions.
.png)
Germany
Germany handed the Knowledge Technology Safety Act 2.0 as an change to the First Act to “enlarge cyber and files security towards the backdrop of increasingly extra frequent and sophisticated cyber-assaults and the persisted digitalisation of on a normal foundation existence.”
.png)
European Union
The European Union Company for Cybersecurity (ENISA) launched a July 2021 checklist titled “Thought the enlarge in Supply Chain Safety Attacks.” The checklist reviewed 24 utterly different system provide chain assaults and shared solutions that organizations can even aloof put in topic to shield themselves towards assaults.
Helpful Recommendation
As governments in the end acknowledge the dangers associated with unmanaged system provide chains, they are aggressively pursuing mandates that align the system commerce with utterly different manufacturing sectors. Snoop on what’s taking place legislatively in your market, safe obsessive about the public conversations and be prepared to have changes to your growth practices accordingly.
Dig Deeper and Procure the Fat Narrative
Engineers are making to take into accounta good series of digital decisions at every allotment of the DevSecOps rate movement that they did not must take into consideration correct a year previously. Thought the trend to optimize these decisions and how they affect the elevated system provide chain is paramount to an organization’s success.
Dig into the fat checklist for extra insights, diagnosis and guidance round developing optimum system provide chains.