
What to achieve when your computer is stolen (and the draw one can prepare for it)
If your computer is stolen, you would maybe well must act like a flash to protect up your individual data stable—and actions you mediate sooner than the hijacking would maybe well also moreover be compulsory.
Nowadays’s Most efficient Tech Deals
Picked by PCWorld’s Editors
Top Deals On Sizable Products
Picked by Techconnect’s Editors
Having your computer stolen isn’t just tense because you wish change a luxurious share of hardware—it moreover poses a likelihood to your digital safety. Fortunately, there are steps you would maybe well also mediate to protect yourself both sooner than and after your computer goes lacking.
Read on to study about how one can prepare yourself in opposition to the likelihood of notebook theft, how one can yelp the theft if your computer is stolen, and the draw one can guard your data after it’s within the hands of thieves.
How to prepare for likely computer theft
Obviously, no person expects their computer to earn stolen, but it absolutely can happen to anybody. It’s essential to mediate steps to protect yourself whereas your computer (and your sensitive data) is quiet to your possession, because it makes recovering from a notebook theft noteworthy more straightforward. In remark, you ought to quiet form definite to:
Encrypt your data
You would maybe well encrypt your exhausting pressure so that no one can access your sensitive data (adore saved passwords and your bank card data) even within the event that they’ve physical access to your computer.
If your computer is working Windows, mediate a short time to space up BitLocker, that can encrypt your pressure. You’ll must consume a password to access your data, so form definite to have a look in any respect of the identical outdated password ideal practices. (Above all, don’t write it on a put up-it assert and stick it for your computer.)
Within the event you’re originate to the usage of third occasion instrument, you would maybe well also moreover download Absolute Dwelling & Build of enterprise (formerly LoJack for Laptops). Besides to to encrypting your pressure, it moreover makes it more straightforward to mediate one of the essential most opposite measures described on this article, equivalent to tracing your computer’s popularity and remotely deleting your data.
Secure a novel backup
You ought to quiet continually abet up your data so that if any individual steals your computer, your recordsdata aren’t lost forever. You ought to quiet be doing this even in case you’re not concerned with computer theft, since data would maybe well also moreover be lost or broken in dozens of a entire lot of strategies.
To search strategies to abet up your data extra successfully, search for our guides on the ideal backup instrument for Windows and the ideal online backup products and companies.
Enable your computer’s monitoring characteristic
Lastly, you ought to quiet enable your computer’s monitoring characteristic. If it’s stolen, you would maybe well also use this to stumble on and lock it. In Windows 10, this characteristic is is believed as Pick up My Instrument; in macOS, it’s just known as Pick up My.
To make use of the Pick up My Instrument characteristic in Windows, your computer wants to be logged into a Microsoft Legend and popularity products and companies must be enabled.
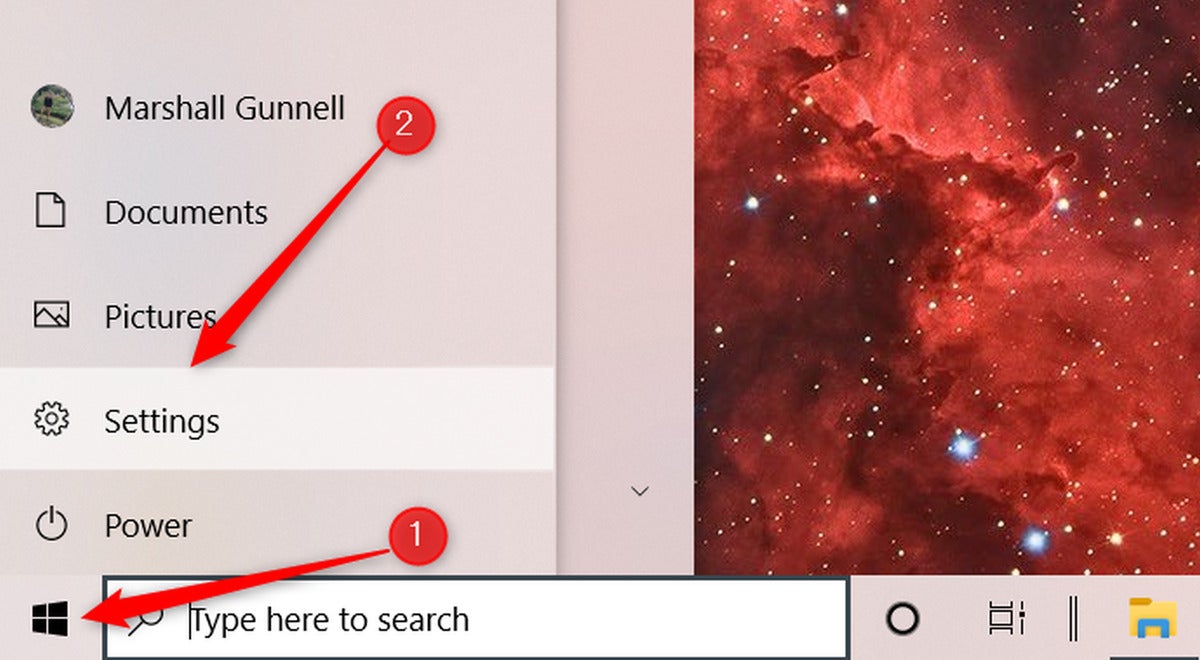 Marshall Gunnell/IDG
Marshall Gunnell/IDGTo enable this characteristic — which, to be clear, it be essential to achieve sooner than your computer is stolen—click the Start Menu within the bottom-left nook of your desktop and then click Settings.
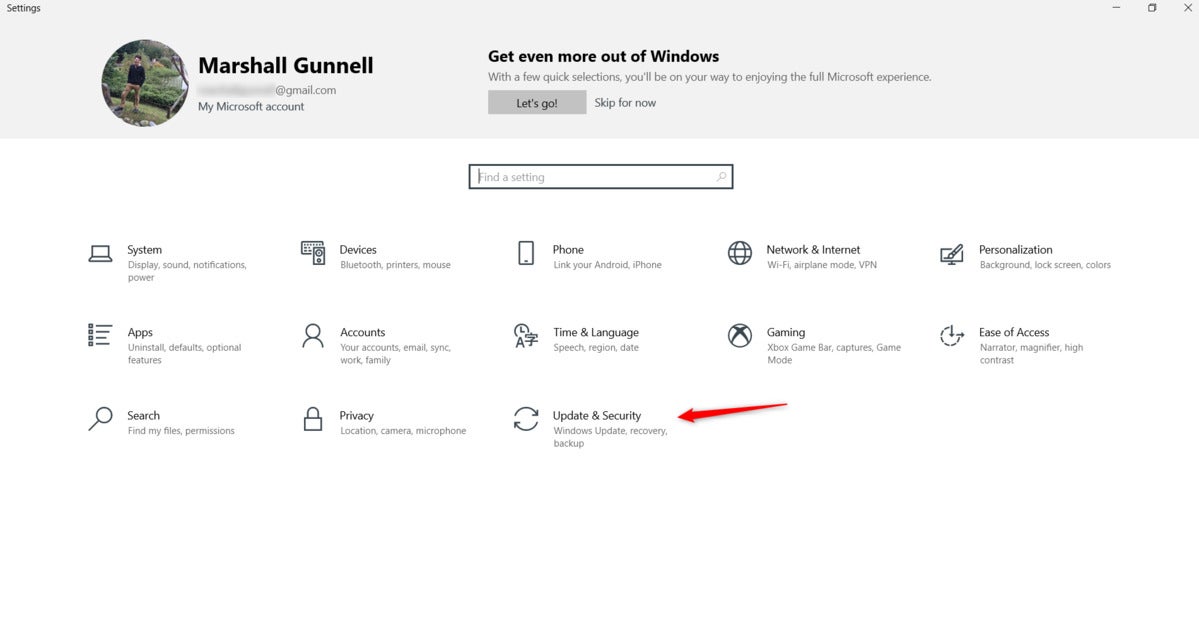 Marshall Gunnell/IDG
Marshall Gunnell/IDGWithin the Settings cowl, click the button that claims Change & safety.
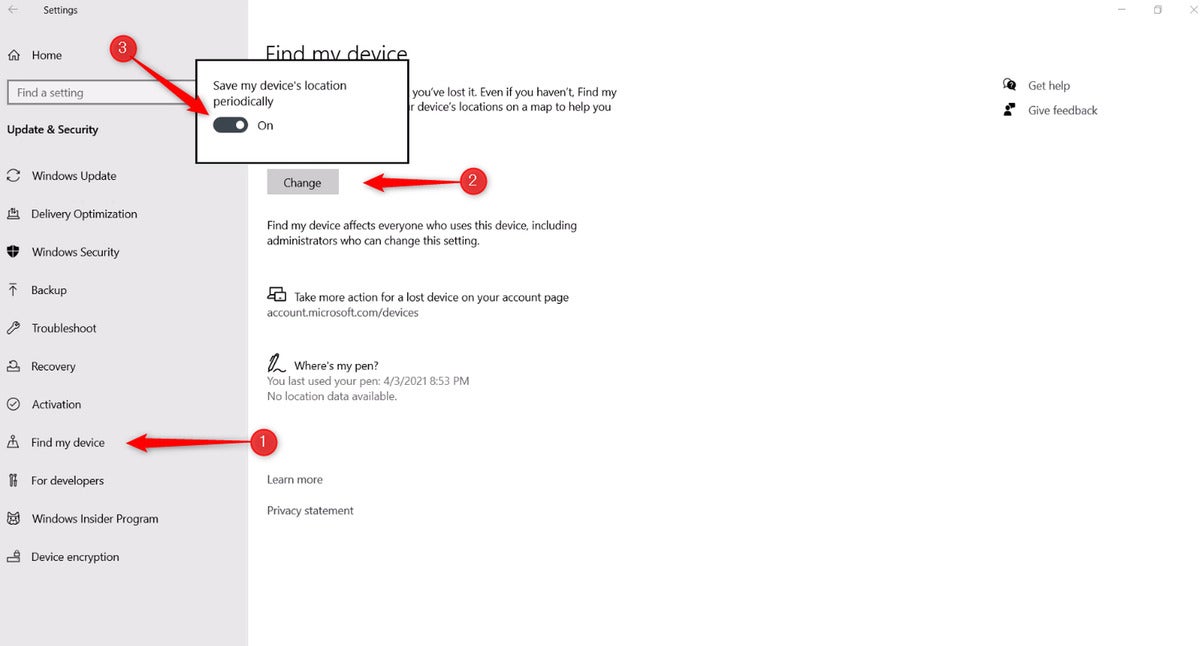 Marshall Gunnell/IDG
Marshall Gunnell/IDGSubsequent, click Pick up My Instrument within the sidebar. Click the button on the next cowl that claims “Change,” and at final, toggle the slider to the “On” space under “Build my instrument’s popularity periodically.”
What to achieve when your computer will get stolen
If any individual does elevate your computer, you wish act like a flash. Remove these steps:
- Detect and lock your computer
- Relate the authorities
- Offer protection to your individual data
1. Detect and lock your computer
You would maybe well most efficient attain this in case you enabled the “Pick up My Instrument” characteristic, as described above.
To stumble for your computer after it’s stolen, reveal over with the gadgets net page for your fable on Microsoft’s net order. Click the tab that claims “Pick up My Instrument” and consume your computer (search the name it seemed under whereas you connected it to your local community). Click “Pick up.”
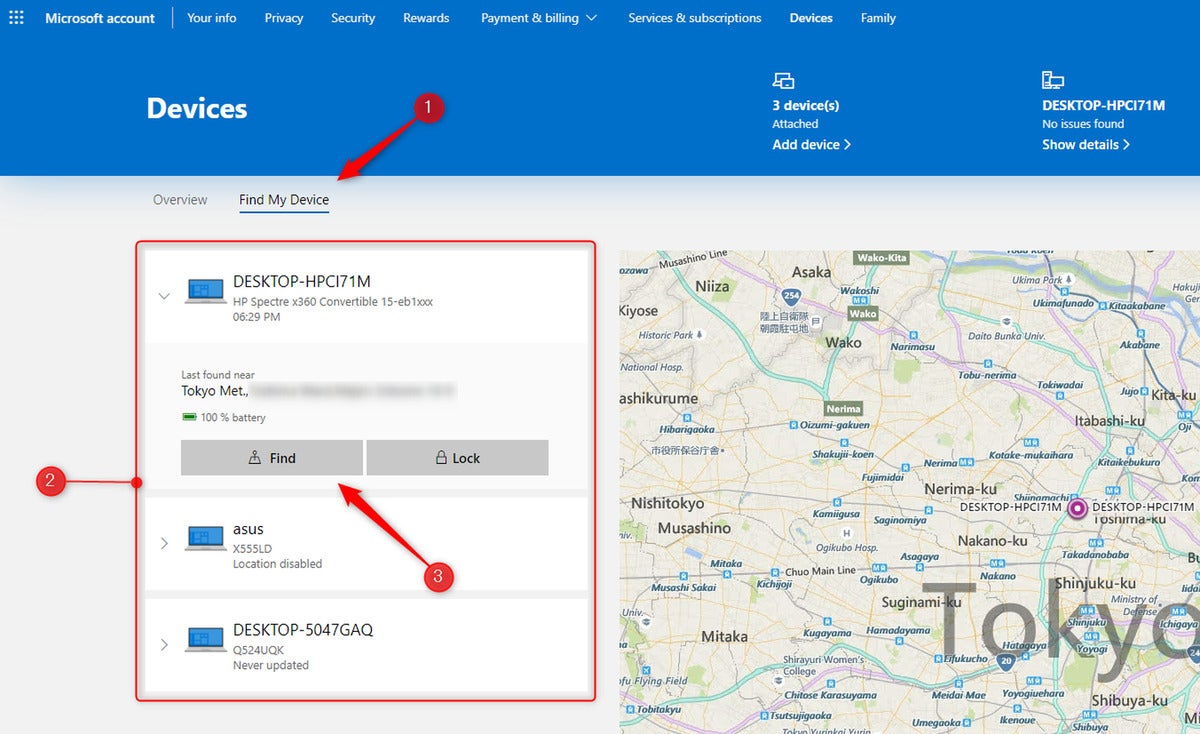 Marshall Gunnell/IDG
Marshall Gunnell/IDGIf everything goes essentially based on scheme, Microsoft will reward a scheme exhibiting your computer’s popularity. Remove a screenshot—you’ll are looking out to construct it whereas you yelp the theft to the authorities, which you ought to quiet attain next.
To provide protection to your data, click your computer on the scheme and click on Lock > Subsequent. This would well well also dwell anybody from the usage of your computer till you release it. That includes you, so if your computer will get returned to you (protect your fingers crossed) you’ll must signal abet into your Microsoft fable sooner than you would maybe well also log in.
2. Myth the theft to the authorities
Whereas you’ve taken steps to song your computer, it’s time to let the authorities know what took space.
File a police yelp
It potentially goes with out asserting that you ought to quiet yelp the theft to the police. You would maybe well attain this by calling or visiting your local police department’s place of work, but you’ll moreover potentially be ready to file a theft yelp through their net order.
As soon as the police approves your yelp, set a request to for a copy. Maintain the case number, the officer assigned to your yelp, and the police order’s phone number. You’ll must construct this data to the opposite authorities, equivalent to your insurance firm and the computer manufacturer.
State your financial institution
Within the event you ever store online, your bank card data is also saved for your computer. Contact your financial institution in the present day to freeze your cards and dwell folks from gaining access to your online accounts.
You ought to quiet attain this even in case you encrypted your exhausting pressure. There’s a factual likelihood that doing so averted the thieves from stealing your data, but it absolutely’s quiet better to be safe.
Whereas you deliver your financial institution, they’ll abet video display your accounts for suspicious exercise. You ought to quiet moreover protect a shut anticipate for your financial institution statements for the next few months, just in case.
 Skynesher / Getty Photos
Skynesher / Getty PhotosFile a assert along with your insurance firm
Within the event you’ve gotten owners or renters insurance, you would maybe well also file an insurance assert for your stolen computer. Be ready to construct that reproduction of your police yelp—your insurance firm will potentially set a request to to see it.
Each owners and renters insurance cowl theft of private property, which comprises your computer. This implies that if it became once a work computer, you would maybe well not be ready to file a assert, since your employer’s property technically doesn’t rely as your “private” belongings. If your work computer will get stolen, contact your employer as a replace and search for within the event that they’ll provide a new one.
Contact your computer manufacturer
Test your manufacturer’s net order and search for within the event that they’ve a hotline you would maybe well also name to yelp stolen gadgets. Within the event that they attain, name them and expose them your computer’s serial number.
The manufacturer will flag your computer of their draw and deliver the police if the thief contacts tech make stronger or tries to file a guaranty assert for your stolen computer.
3. Offer protection to your individual data
As you’ve potentially gathered, when your computer will get stolen, it puts all your data in nervousness. Remove the next steps to protect yourself:
Wipe your data
If your lost instrument is hooked up to the info superhighway, you is also ready to remotely erase your data.
Within the event you’re the usage of macOS and delight in the “Pick up My” characteristic enabled, you would maybe well also tag your instrument as lost and remotely erase it the usage of a same direction of to “Pick up My Instrument,” outlined above. This would well well also moreover lock your instrument and disable Apple Pay.
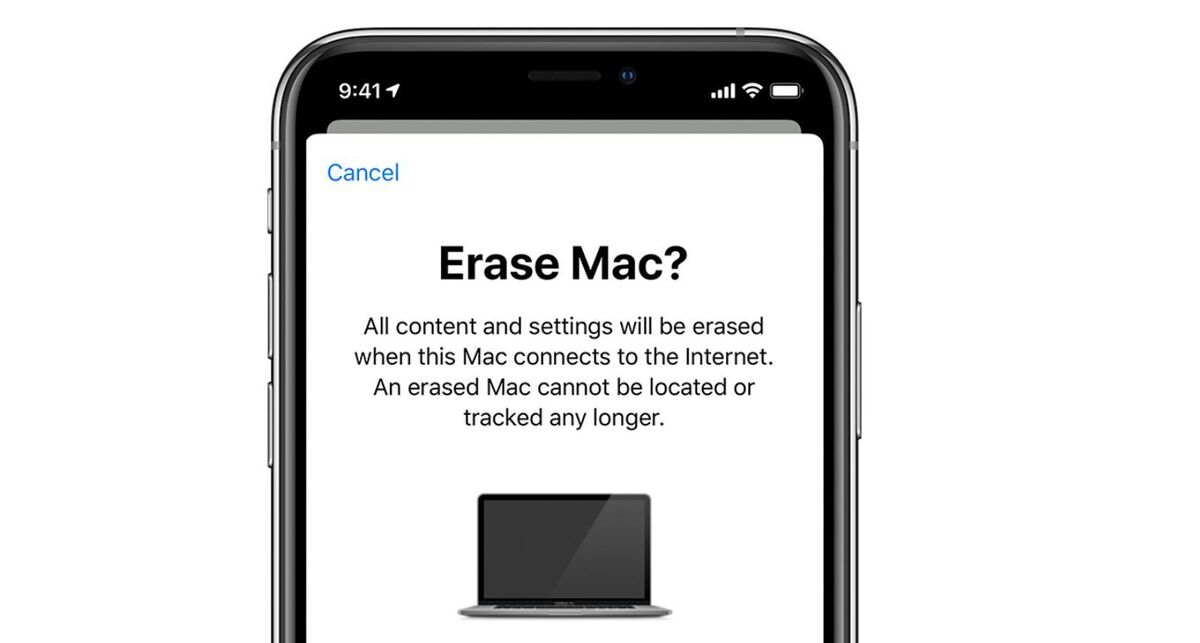 Apple
Apple Within the event you’re on Windows and you earn aside within the Absolute Dwelling & Build of enterprise instrument suite beforehand urged, you would maybe well also use that to wipe your data as successfully.
Within the event you’re lucky adequate to earn better your computer, you ought to quiet mediate into consideration wiping it again, in case any individual set in spyware that can allow them to access your data remotely. Guarantee you’re truly deleting the info—it’s not adequate to simply bound just a few recordsdata to the trash.
Change your passwords
Log into your online accounts and commerce your passwords. You ought to quiet attain this for every fable you would maybe well also keep in mind gaining access to from your computer, but pay remark attention to your electronic mail, financial institution logins, and social media profiles.
Need to you’re doing this, form definite not to change the autofill characteristic so that the passwords for your lacking computer aren’t synced and updated.
Within the event you expend a password supervisor adore LastPass, 1Password, or Dashlane, you would maybe well also wipe and uninstall all your passwords which will be synced along with your lost computer. (Inserting in right here is one thing else that must be performed before time).
Disable autofill and clear your taking a peek data
After altering your passwords, delete your browser data, equivalent to your autofill settings and taking a peek history.
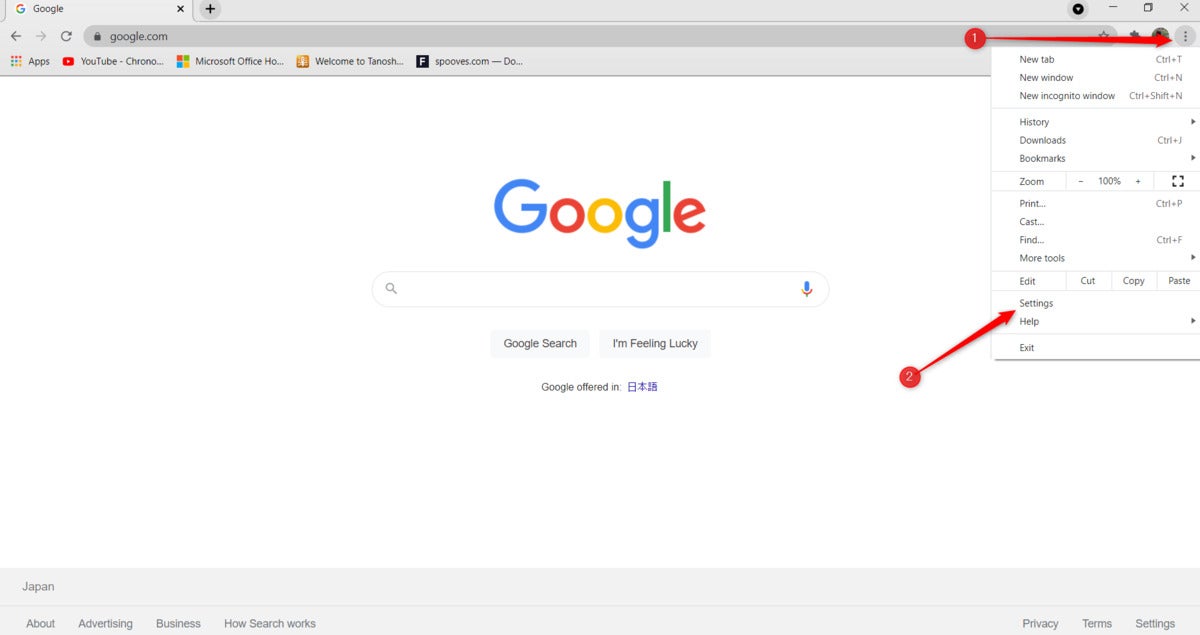 Marshall Gunnell/IDG
Marshall Gunnell/IDGWithin the event you’re the usage of Chrome, you would maybe well also attain this remotely by opening the browser menu (click the three dots within the discontinuance-appropriate nook of the window) and clicking Settings.
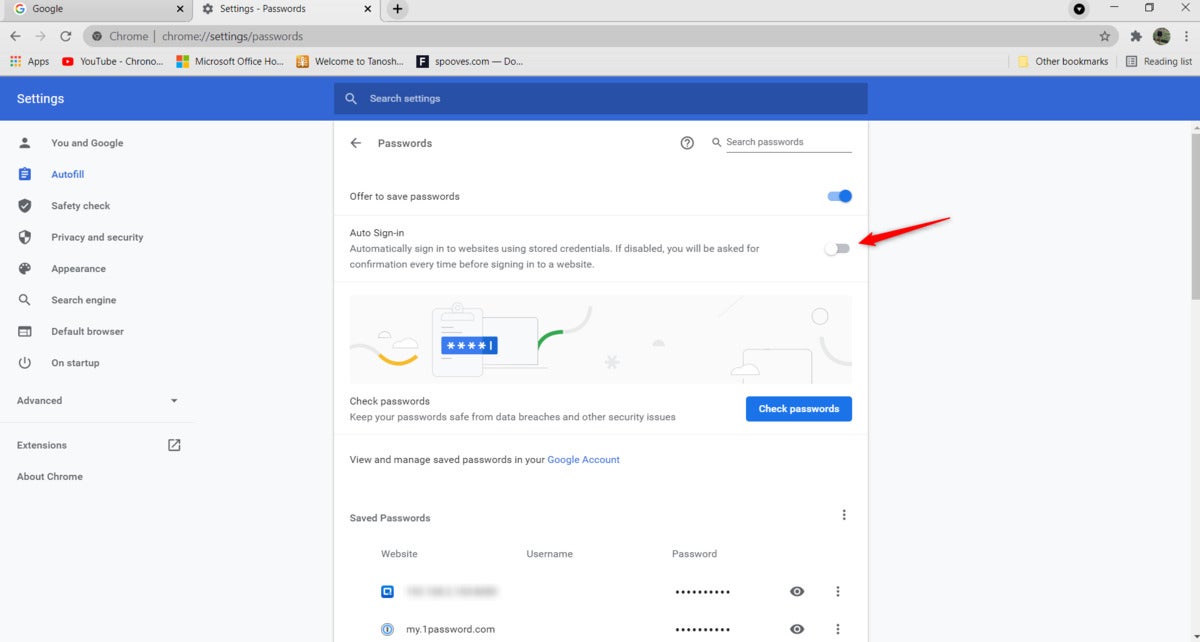 Marshall Gunnell/IDG
Marshall Gunnell/IDGSubsequent, click Autofill > Passwords and then toggle the slider next to “Auto Signal-in” to the off space.
Deauthorize your fable and gadgets
Within the event you expend a Google fable, signal out of Chrome remotely to deauthorize your instrument. Firefox and Safari moreover allow some distance-off signal-outs.
Within the event you’re the usage of an Apple computer, you would maybe well also remotely log out of any instrument signed in along with your Apple ID. Guarantee you moreover flip off auto-sync between your linked gadgets to dwell your sensitive data from being synced for your lacking computer.
It’s nerve-wracking to sign your computer’s been stolen, but don’t nervousness. Even supposing there’s no draw to expose whether you’ll search for it again, in case you dwell aloof and act like a flash, there’s a extraordinarily factual likelihood you’ll be ready to safeguard your data and provide yourself with protection from consequences past the fast loss. And in case you wind up being unable to bodily earn better your pilfered notebook, our data to the ideal laptops allow you to search your next one.
Exhibit: Need to you score one thing after clicking hyperlinks in our articles, we would maybe well also abolish a minute rate. Read our affiliate link policy for further minute print.